2024 Cybersecurity Buyers Report: Insights and Guidance for Cyber Builders - Part 2
Understanding Cybersecurity Buying: From PoC to Purchase Decisions
Hello, Cyber Builders 🖖
In the first part of our exploration of the “2024 Cybersecurity Buyers Report,” we uncovered intriguing insights about team sizes, the rising trend of outsourcing, and the critical balance between resiliency and proactive risk management.
As we continue to navigate this comprehensive report, Part 2 is driving us to examine the mechanics of cybersecurity buying processes as seen through the customers’ lens.
In Part 2, we’ll delve into the nuances of Proof of Concept (PoC), the intricate sales cycle, buying decisions, and the maturity of cybersecurity practices from the customers’ perspectives. These factors are crucial in understanding what tools and strategies are being adopted, how organizations make these critical decisions, and what influences their thinking.
Before we zoom in, can I ask a favor? Cyber Builders is the newsletter of CyGO Entrepreneurs, the First Cybersecurity European Studio.
It will help us build our community of security practitioners and future product design partners if you share the newsletter with other security-interested persons. Just hit the above button 👇 and share with three contacts. Thanks a ton 💪
In this Post
How long is the sales cycle for Cyber Builders, and Why
Webinars are still an essential practice
IT leaders are part of the decision process
And people trust “too much” their EDR usage
Long Sales Cycle in Cybersecurity Solution Buying
When purchasing cybersecurity solutions, CISOs and IT leaders tend to take their time and choose carefully. The “2024 Cybersecurity Buyers Report” reveals that most prospects are entrenched in a 6–12-month purchase cycle. This extended period is something that Cyber Builders must anticipate and prepare for; it is also a fact to challenge any salesperson (SDR or AM) who would come to you claiming they will sign next week the customer they met this week.
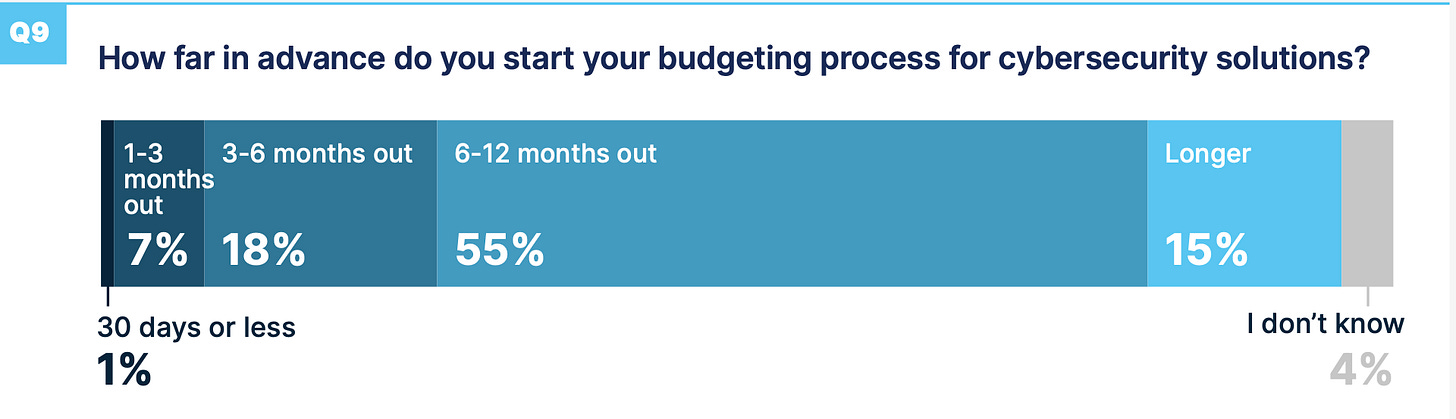
Speaking of budgeting, it’s essential to note that 86% of organizations adhere to annual budget cycles. Cyber Builders must focus on whether a budget is prepared for this.
Further complicating the procurement landscape is the vendor selection phase, which, for 44% of respondents, lasts between 3 and 6 months. We can think of this stage as critical as organizations sift through various vendors, assessing which best meets their specific security needs, offers the most robust solutions, and provides value for money.
But we can also wonder why it is so hard to choose cybersecurity solutions. It takes a lot of time and reputation to be on this shortlist and eventually evaluated. Still, it takes six months to get selected. I would argue it is hard for customers to assess and choose.
Testing cybersecurity product is hard
If you think about it, how can a five-person team replicate threat actors and test effectively whether a product will defend them? How can they evaluate integrating the new product into their existing processes without integrating the full system?
Decision-Making Circle - Don’t Forget IT and Executive Leaders
When purchasing cybersecurity solutions, the typical focus tends to narrow down on the CISOs as the primary decision-makers. However, this assumption overlooks the significant roles that other key organizational figures play in this critical process. While CISOs are undoubtedly pivotal, the influence of IT management and C-level executives, particularly CEOs and CFOs, is equally consequential.
The "2024 Cybersecurity Buyers Report" states
In organizations with 500 or more employees, as shown above, IT management still plays a lead role, followed by the CISO, the security management teams, and C-level executives.
This hierarchy of influence underscores that while security-specific leadership is critical, the broader IT management team possesses substantial sway over buying decisions. Cybersecurity is still an IT topic—even many would love to connect it to the broader topics of resilience, general risk management, or physical security.
Moreover, the influence of top executives becomes even more pronounced in larger organizations.
“Collectively, in organizations over 5,000, the CTO/CFO/CEO roles make the call in 20% of the companies surveyed.”
This trend indicates that cybersecurity is not just a technical issue but a business one, deeply intertwined with financial health and executive strategy.
Webinars and Online Presence Are Essential
Webinars remain the preferred method for learning about new cybersecurity solutions. I remember running popular webinars on OT security in 2015. It was “the” way to appear as a modern vendor….. It looks like it is still a good way!
Following closely behind, recommendations from industry peers and discussions on platforms like Reddit and other websites rank as the second and third most popular sources for information.
This underlines the importance of maintaining a solid online presence and leveraging the power of social media and industry ambassadors to enhance visibility and credibility. I feel it is often overlooked by many sales-led teams who think they will win by “meeting customers.” These practitioners will open their browsers before and after the meeting, you can be sure.
Running a Proof of Concept in Cybersecurity - A Mandatory Practice
Running a Proof of Concept (PoC) has become a mandatory and de facto standard in cybersecurity solution buying. It’s not just about understanding the product’s features but also demonstrating how it integrates into existing IT systems.
The scope of the PoC, particularly its features and potential for risk reduction, is crucial. Buyers must see firsthand how a solution performs in their unique environment and how it addresses specific security challenges.
Additionally, integration plays a crucial role. A new piece of software must fit into an organization’s existing IT. If not, why do the practitioners would bother to buy them?
Concluding Remarks on the Cybersecurity Buyers Report
I choose not to cover these aspects, but the report delves into the specifics of security controls and detection mechanisms and presents interesting statistics for Cyber Builders in various fields.
What strikes me the most is a quote from IBM Security:
According to IBM Security, the average time to contain an incident in 2023 was 73 days. However, respondents may have an unrealistic perception of their incident response capabilities as most (98%) responded that they can respond to and contain threats on endpoints in less than a day.
This may also be attributed to an overreliance on EDR and antimalware tools to contain endpoint security incidents fully. It underscores a significant disconnect between perceived and actual response capabilities, highlighting the need for a more realistic assessment of security tools and team readiness in the face of incidents.
There is a lot still to be done in the cybersecurity market… Work Cyber Builders!
Laurent 💚









Great insights!