AI in Cybersecurity: Not a Magic Wand, But a Multiplier
DARPA AIxCC - Open-source CRSs finding and patching flaws at scale—this is Intelligent Security
Hello Cyber Builders 🖖
This week, I’m announcing a new series on Intelligent Security. That’s the name we used at CyGO Entrepreneurs for something I deeply believe in: how AI can enhance and scale cybersecurity operations.
If you’ve followed RSA25 or Black Hat this year, you’ve noticed it—vendors everywhere are pitching AI agents and AI copilots for security. Exciting, yes. But let’s not fool ourselves: AI is not a magic wand. What it is, though, is a powerful multiplier. And when you’re facing scaling challenges in risk and governance, identity security, OT, or security operations, multipliers matter more than silver bullets.
That’s what I want to explore in this series. Before we get lost in the noise of new features, let’s pause and ask:
Why do we actually need AI here?
What can AI realistically do today?
How do we separate real progress from clever marketing?
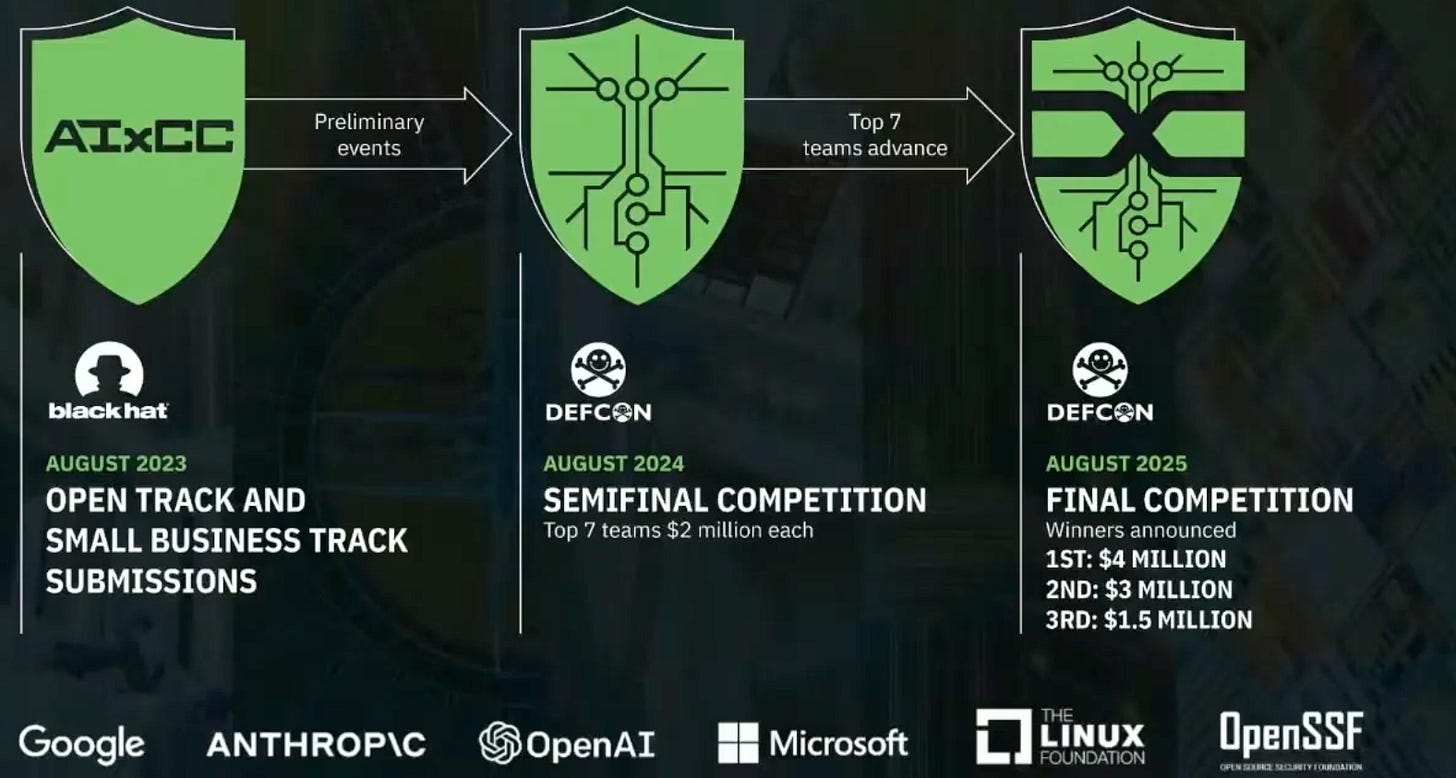
While I’m refining the key themes for this series, for this week, I want to leave you with something fascinating: the AIxCC Challenge, presented at DEF CON this August. I will give you an overview, but you can learn more and watch the full 1H video on the dedicated website.
Introducting AIxCC
This challenge, run by DARPA, asks teams to use AI to find and patch vulnerabilities in source code. The catch? These aren’t obvious bugs. They’re sophisticated issues carefully planted in reference code—the kind of vulnerabilities that keep CISOs awake at night.
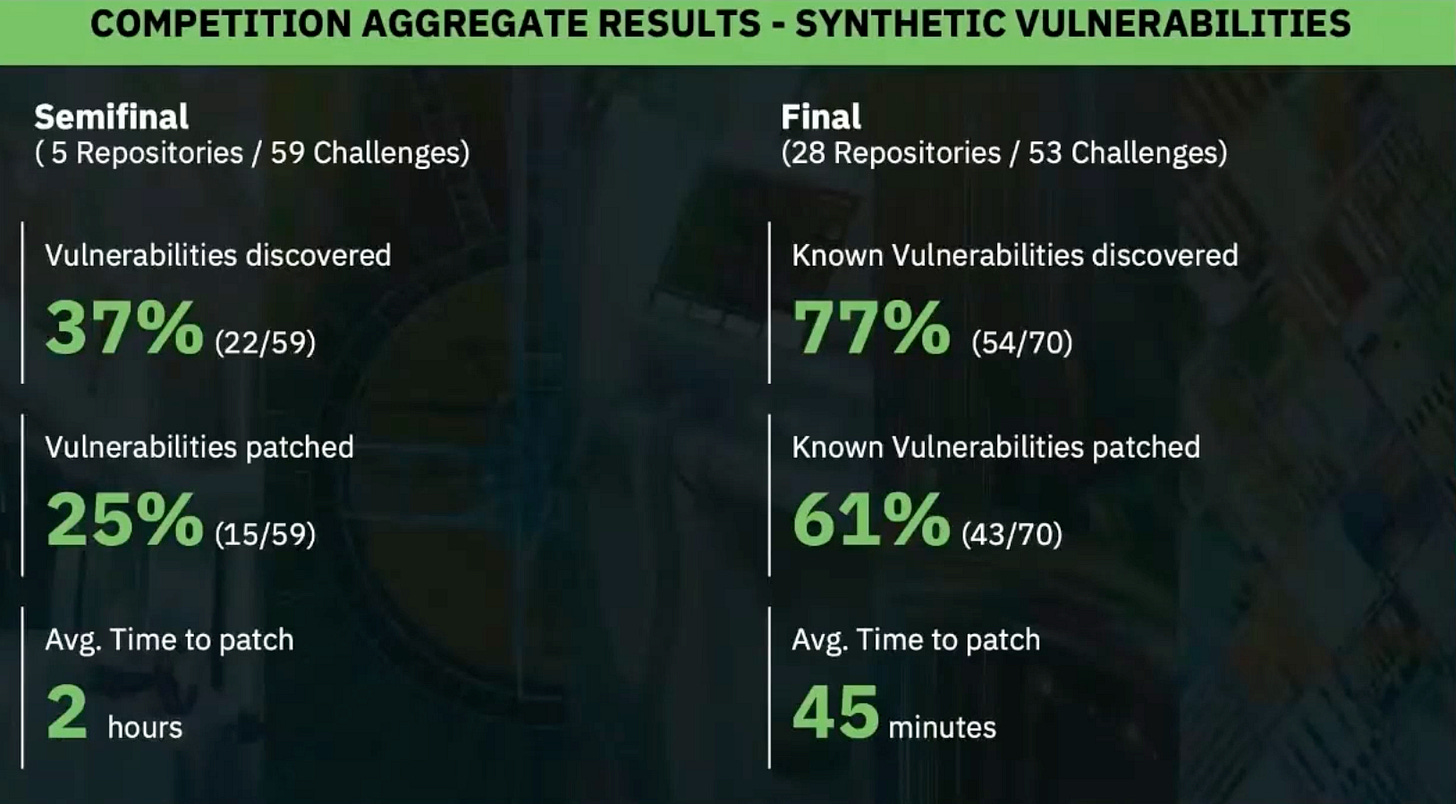
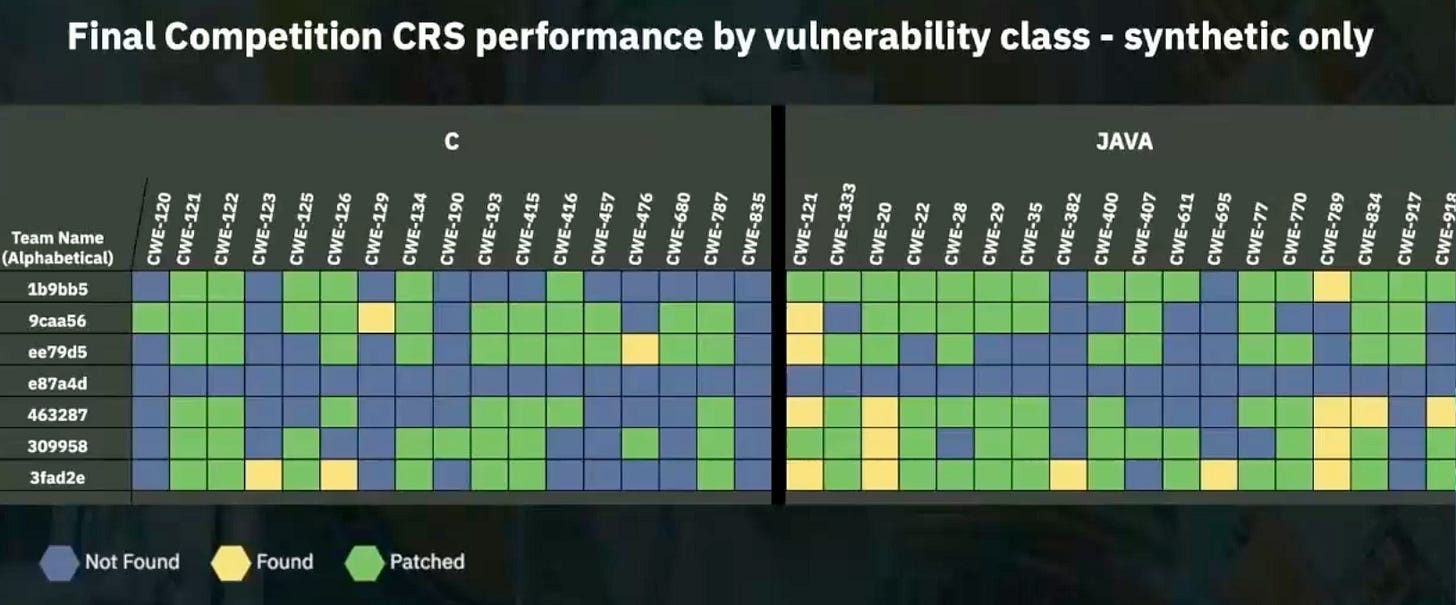
These teams didn’t just walk away with millions. They proved something bigger. Their Cyber Reasoning Systems (CRSs) managed to find 77% of the vulnerabilities and generate correct patches for 61% of them—inside more than 54 million lines of code. Let that sink in. AI systems are digging through mountains of code and fixing flaws at scale.
And here’s the best part: all seven teams are making their systems open source. Which means you can study them, adapt them, apply them, and yes—build on top of them.
As Andrew Carney, the AIxCC Program Manager, put it, the competition showed us what’s now possible.
And here’s why it matters. First, the challenge has been running for two years. The results are open source—meaning we can all study and learn from them.
Moreover, they have not only identified the issues but also patched them, demonstrating a proactive approach to problem-solving.
All this is only for 152$ per found and patched issue
My personal note on this is that when you look at the CRS repositories, you realize that AI is not a magic wand doing expert work by itself. It acts as a multiplier for best practices. It orchestrates many tools, evaluates the results of existing tools (like a fuzzer, for example), and determines the next best action to take.
So, you shouldn't view AI as a standalone system. Instead, it will work like a doctor treating a patient, using a team of experts and their tools.
That’s a glimpse of Intelligent Security in action. And it’s a reminder: AI in cyber is not just hype. It’s happening now.
Conclusion
What the AIxCC challenge proved is simple: AI is no longer just an assistant—it’s a force multiplier that can change the economics of cybersecurity. Finding and patching vulnerabilities at scale, for just $152 per issue, is not science fiction. It’s here. It’s working. And it’s open for everyone to study and build on.
This is Intelligent Security in action. Not buzzwords, not marketing slides—real systems solving real problems.
And in the weeks ahead, we’ll dive deeper into what Intelligent Security means for risk and governance, identity, OT, and security operations. The tools are here. The question is: what will you build with them?
Stay tuned.
Laurent 💚
Teaser (1 minute)
1st - Team Atlanta (2 minutes)
Everything they do is open-source, but they always have difficulties justifying it! Keep going, guys.
2nd - Team Trail of Bits (2 minutes)
Big proponents of open source, passionate about helping the “poor open-source maintainers who are quite alone to fix all the vulnerabilities”. Thanks for your work!
3rd - Team Theori (2 minutes)
Cybersecurity and AI professionals with a shared background attending Carnegie Mellon University and succeeding in DEF CON Capture the Flag more than anyone else!