The Future of Cybersecurity: Everyone is a Software Producer
As software takes command, a new cybersecurity battlefield - software product security and their supply chain
Hi Cyber Builders 👉🏼
This week, I am looking at how ubiquitous software is and what it means for cybersecurity. The application security market is booming with significant acquisitions and big fundraising rounds.
As an example, see
Looking just at these numbers is not giving you an accurate picture. We need to dive deeper and ask why there is so much interest from the industry and the governments in securing software.
This post is the first of a new series. I previously wrote about Cybersecurity for SMB and Cyber and AI as a series. Before we dive in, can I ask a favor? Please share Cyber Builders with two (or more) colleagues. Please help me grow the readership and increase collaboration to build the future of cybersecurity.
In this post…
As software is becoming ubiquitous in modern life, it's transforming how businesses operate and how we think about and approach cybersecurity.
This shift carries significant implications for cybersecurity, making it a critical concern for all businesses as they inherently assume responsibility for the security of their software products.
This post explores this evolving landscape, the increasing incidents of software supply chain attacks, and tightening regulatory frameworks,
The proactive management of product security can yield significant competitive advantages. The series will continue to delve deeper into these themes in subsequent posts.
Software takes command
In this age of digitalization and networks, software has become integral to every aspect of our lives. Software is at the heart of every innovation and operation, from websites to mobile applications industrial systems to consumer devices. It has enabled the rise of disruptive companies like Uber, Airbnb, and Netflix, fundamentally reshaping entire industries.
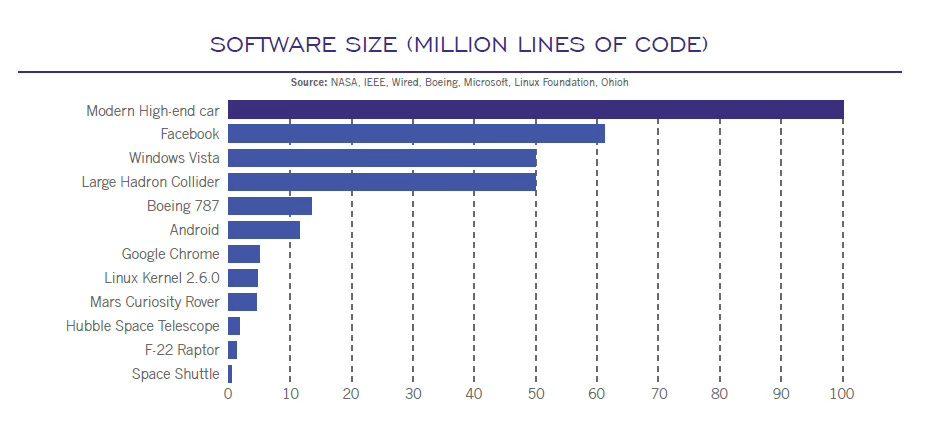
Indeed, the prevalence of software is such that it has become inseparable from the products and services we use. Even the most traditional sectors, such as aviation, automotive, and manufacturing, have been transformed into massive software entities. The lines of code in a modern car outnumber those in a personal computer.
This ubiquity of software has profound implications for businesses of all sizes.
All businesses today depend on software to communicate, organize themselves, and create value in all organizations, whether large or small. IT departments are in place to help organize and implement these software solutions.
It is apparent and not new when I say this. It is accurate, and Marc Andreessen prophetized it long ago - see “Why Software Is Eating the World.”
But I believe that all companies are not just software consumers; everyone is becoming a software producer. To understand this, let's look at how companies historically used software.
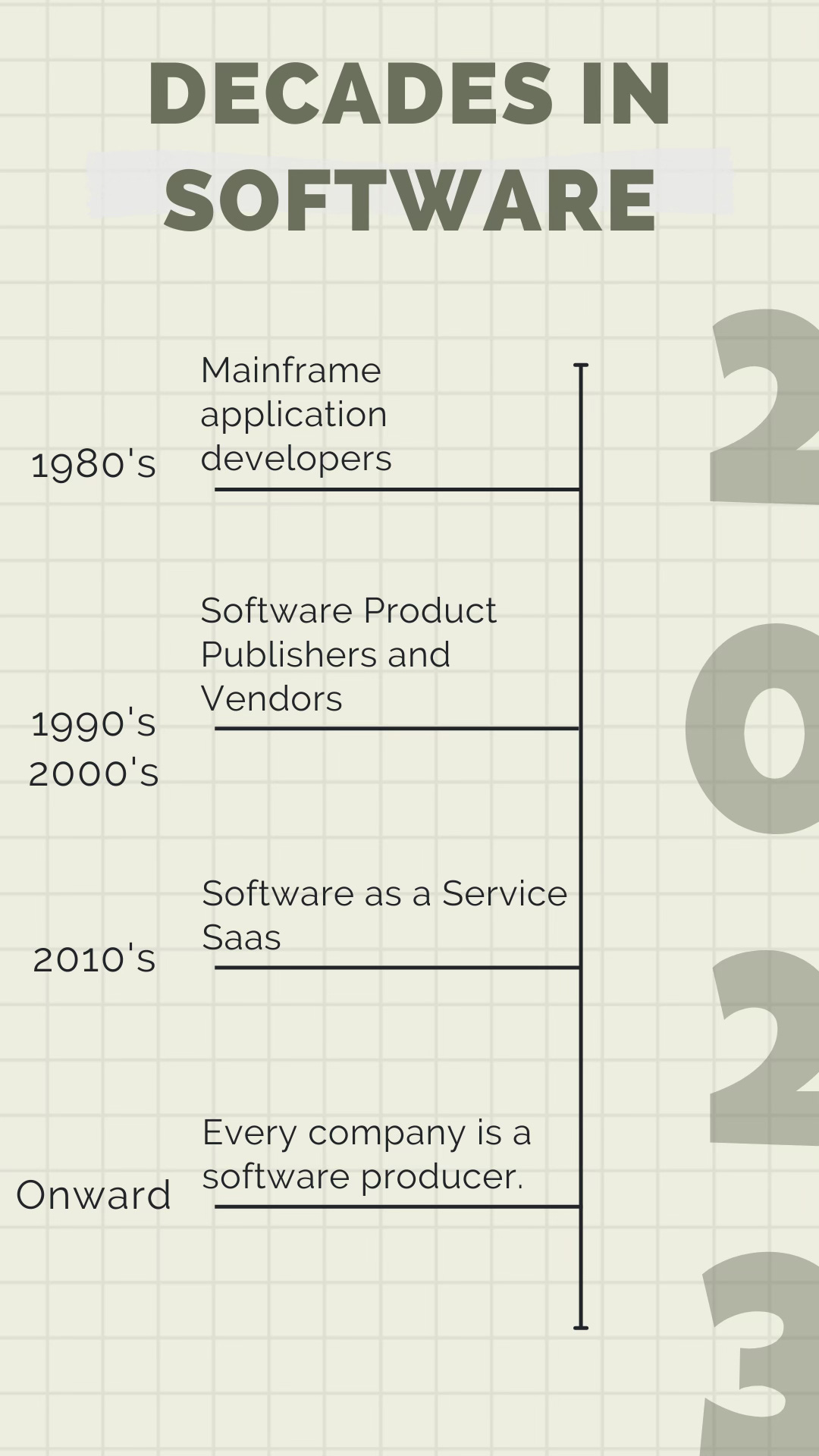
Between the 80s and 90s, the first computers or mainframes were developed. They were monolithic and required each company to build its applications on these mainframes. They were primarily deployed in large organizations. The world of SMBs was excluded from using these technologies. At that time, large enterprises were all software producers.
Then, in the late 80s and throughout the 90s and 2000s, the software publisher industry emerged, where software development was entrusted to specialists who had a relatively large engineering team with experienced engineers, architects, database administrators, as well as a marketing and sales team to commercialize these software solutions. Software became a product. It was purchased, installed, and connected to other software systems in the company's information system, such as operating systems like Windows or databases, etc.
In the mid-2000s and the past decade, there has been a shift towards software as a service (SaaS), which marks a new change. Software is no longer a product but becomes a service that users consume through a monthly subscription. SaaS simplifies implementation, eliminating the need for long phases, deployments, integration, and interconnection, as the publishers and platform providers take care of all these services. SaaS provides more comprehensive services, stores data, archives, and backups, and makes software consumption even more accessible for companies.
Throughout these three stages of evolution, the software has penetrated the entire economy, starting with large enterprises. The software publisher and SaaS models enabled SMBs and freelancers to use software massively.

All companies are now software producers.
As we draw closer to an inevitable future, the transformation of all businesses into software creators is imminent. Companies constantly evolve their business models by integrating digital assets into their frameworks. By leveraging software to conduct complex data calculations, insurance companies offer better policies and gain a deeper understanding of their customers. Similarly, supermarkets encourage customer loyalty through mobile applications, enabling customers to maintain a relationship with their preferred brand. We cannot forget the ecological transformation, which necessitates decreased energy consumption, recycling, and the establishment of a circular economy. The software we create is intended to engage greater information exchange and foster connectivity among individuals, customers, and suppliers.
No sector of the economy can claim exemption from becoming a software creator. It is even easier today with the advent of cloud computing, low-code or no-code platforms, and other technologies. You don’t need to set upfront CAPEX with services housed in private data centers (dozens of thousands of dollars/euros of CAPEX and OPEX). You can start small and run your software in a serverless architecture with a quasi-zero upfront cost and a few dollars of operation costs until you get some traction.
Past the era when software development was exclusive to software vendors, we live in a digital age where almost every company is a software producer. This shift has blurred traditional sector boundaries as organizations across all industries embrace software development, either by cultivating in-house teams or seeking the expertise of outsourced software agencies.
Wait, but what about cybersecurity?
The transition from being a consumer to an active software producer has had profound repercussions, particularly cybersecurity.
As every company morphs into a software producer, they inherently assume responsibility for ensuring the security of their software products.
For many companies, it is still not a reality. Many have seen creating new software pieces for their business to differentiate their offering or automate their operations. The software creates value, and its marginal zero cost provides significant returns.
Now, as any mature software producer, companies must add cybersecurity solutions to their stack. While large corporations have advanced in building robust software cybersecurity capabilities, smaller businesses often grapple with insufficient resources to shield themselves from evolving cyber threats.
So how should we help them?
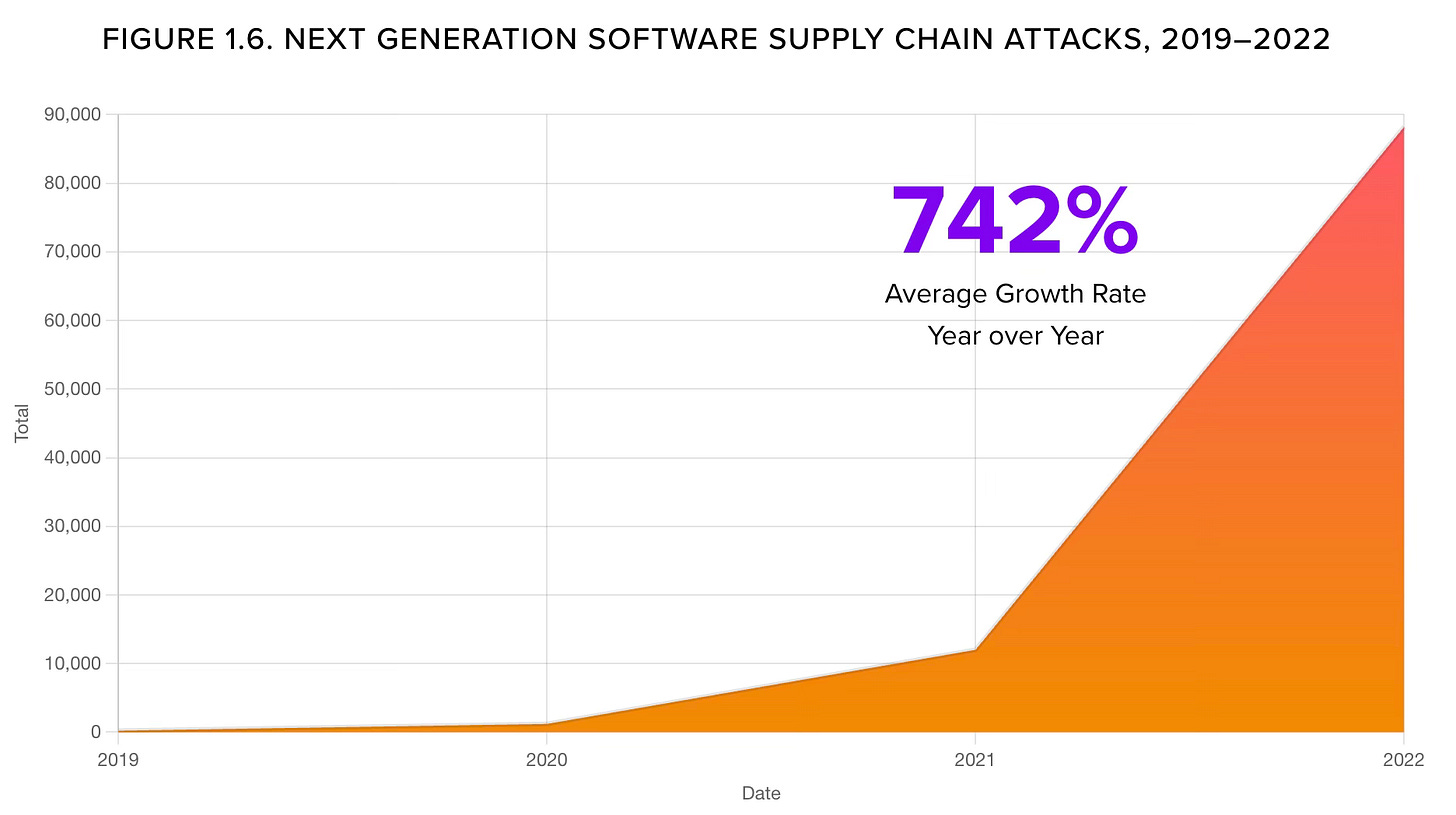
Software supply chains have been under attack for a few years.
Software supply chain attacks refer to malicious activities targeting software development and distribution. In these attacks, threat actors exploit vulnerabilities or weaknesses in the supply chain to inject malicious code or tamper with legitimate software components. By compromising trusted software vendors, open-source libraries, or third-party dependencies, attackers can distribute compromised software to unsuspecting users. This allows them to gain unauthorized access, steal sensitive information, or launch further attacks on targeted organizations or individuals. In recent years, high-profile incidents like SolarWinds and Log4j have highlighted the need for robust security measures throughout the entire software development lifecycle.
Using typosquatting - uploading a malicious software package to a popular repository - attackers can see their malicious code within hundreds or thousands of other applications. Another attack vector is to hijack the credentials of source code and project management solutions (Github, Gitlab, Atlassian) and inject malicious payload within the code itself or at build time. Unfortunately, the creativity of criminals is unbounded to find new ways….
Regulation is ramping up…
Regulatory bodies and governments worldwide are ramping up their efforts to promote cybersecurity as an indispensable aspect of public policy, effectually pushing the responsibility on businesses to assure the impenetrability of their software products. Consequently, this dictates the need for a ‘shift-left’ approach, wherein security is no longer an ancillary consideration but rather an integral component incorporated early on in the software development lifecycle.
In the US, the latest Executive Order - “Enhancing the Security of the Software Supply Chain to Deliver a Secure Government Experience” - emphasizes integrating security practices early in software development. This approach is usually called “Shift Left”.
"Shift left" refers to moving security considerations and activities to the earliest stages of the development lifecycle.
The executive order recognizes that addressing security vulnerabilities and threats at later stages can be costly and time-consuming. Organizations can proactively identify and mitigate risks by implementing security measures, reducing the likelihood of successful cyberattacks. This approach includes conducting security assessments, implementing secure coding practices, performing code reviews, and integrating automated security testing tools. The executive order aims to promote a culture of security awareness and collaboration among developers, security teams, and stakeholders to ensure that security is a fundamental aspect of software development.
This is new in cybersecurity, while the concept has existed in software quality and testing for a decade. It highlights the willingness to have software producers accountable for the security of their software.
The public body aims to reverse the pressure to fix vulnerabilities from consumer to producer. Nowadays, IT administrators are rushing every month to patch software as more and more high-severity vulnerabilities and malware using them are popping up. If the software industry takes a genuine “shift left” approach - something I am still doubtful - it will eventually reduce the burden on IT, as shipped software will be more secure and with less highly impactful vulnerabilities.
Conclusion
As we navigate this evolving landscape, organizations must tackle the organizational and operational challenges associated with product security. This involves establishing dedicated departments and teams responsible for overseeing and managing product security throughout the development and post-production phases.
In the following posts, as security starts with men and women, we will also start by looking at the various people involved in software product security. We will explore the specific regulations shaping this new paradigm, such as the Cyber Resilience Act and Executive Orders. We will examine the pressures exerted by regulatory bodies and customers and how they influence businesses' approach to product security.
Ultimately, the growing importance of product security presents both an immense challenge and a significant opportunity for businesses. Those who can effectively navigate and address the security risks inherent in the software-driven world will gain a competitive edge while protecting their customers and operations. The era of ubiquitous software demands a comprehensive and proactive approach to security.
Laurent 💚




QA is a critical security function, which is often totally missed by everyone. A vulnerability is nothing more than a specific type of defect which is QA realm.