Latest Web3 Exploits - What A World!
A quick overview of blockchains scams and criminals motivations in collaboration with the Netfture Security Team.
Hello Cyber Builders 🖖
I’ve run several articles discussing new techniques like secure multiparty computation. I also shared my views on crypto and many in the cybersecurity community's love-hate relationship regarding crypto, Web3, and blockchain technologies. To conclude this series, for the moment, I’d like to dive deep into some examples of scams, attacks on blockchain, and how criminals are making money by stealing cryptographic assets and cryptocurrencies.
Recently, I met with Nefture, a startup focusing on threat intelligence and helping people protect their crypto assets and secure their wallets. Their technology is impressive, but their knowledge of the various criminals and schemes targeting blockchain and crypto assets is even more remarkable.
After our conversation, we selected three stories that illustrate current Web3 exploits:
1. DMM Bitcoin Hack: On May 31st, the Japanese crypto exchange DMM Bitcoin suffered a $308 million hack due to an unauthorized leak from a company wallet. The attack likely involved a private key exploit, with funds swiftly moved through multiple wallets, potentially linked to the notorious Lazarus Group.
2. Crypto4Winners Ponzi Scheme: On March 9th, Crypto4Winners, promising high returns, was exposed as a $100 million Ponzi scheme. Co-founder Luc Schiltz’s dubious past and the firm’s complex international structure unraveled following a suspicious car accident, leading to fraud and money laundering charges.
3. Pump.Fun Exploit: On May 16th, an employee of Pump, a Solana-based memecoin generator, executed a flash loan attack, stealing $2 million. The attacker, motivated by grievances against his employer, publicly admitted to the crime and was later arrested.
I leave you with all the details provided by the Nefture security team. They contributed the rest of the article!
DMM Bitcoin, The Mysterious $308 Million Hack
On May 31st, centralized Japanese crypto exchange DMM Bitcoin announced that it had fallen victim to an exploit that had cost it a staggering $308 million.
Regarding the exploit itself, DMM Bitcoin chose to stay rather tightlipped, barely acknowledging that it was linked to an “unauthorized leak” from a company wallet and that some of its services would be unavailable during its investigation.

Thankfully, there were enough traces left on-chain to discern what could have gone down that day.
Through blockchain forensics, the blockchain security company Beosin discovered that the attack transaction was a simple direct asset transfer of funds from a DMM Bitcoin wallet to the attacker’s wallet.
The second clue was that the attacker’s address mimicked the first and last characters of an address used as a DMM management address.
From these clues, two main scenarios emerged.
The first one is a multi-sig private key exploit. This transaction did not “exploit” per se, as it was a simple transfer of assets typical of a private key exploit. Nevertheless, underlined Beosin, the transfer could also potentially indicate the exploitation of the signature service of DMM Bitcoin.

The second scenario is an address spoofing attack. As mentioned earlier, the attacker’s and DMM's Bitcoin addresses looked similar, at least on the surface. This could indicate that, for an unknown reason, the transaction was initiated by DMM Bitcoin. Still, instead of the $308 million being transferred to another DMM Bitcoin address, the sender was led to send the funds to the attacker’s address.
The attacker's mimicry of a DMM address could also be explained by trying to avoid security screening that could have stopped the transfer authorization within the DMM ecosystem.
The most likely scenario seems to be a private key exploit, as the transferred amount is enormous, and the norm for any transfer of this extent is to send some funds as a test. It’s also hard to envision that a crypto exchange of this size would not whitelist their addresses. Plus, DMM Bitcoin chose to address this hack as an “unauthorized leak,” hinting that it was more likely than not a private key leak.
After the hack, the attacker quickly dispatched the funds through ten Bitcoin wallets.

On July 15th, crypto sleuth ZachXBT alleged that the DMM Bitcoin hack was the work of the Lazarus Group after investigating the case and detecting ‘similarities in laundering techniques and off-chain indicators’ with Lazarus.

Crypto4winners, A $100 Million Ponzi?
On March 9th, the investment firm Crypto4Winners, which promised 3–20% monthly returns, announced that they had fallen victim to an exploit.

Due to the exploit, Crypto4Winners found itself in the difficult position of no longer being able to allow ‘process fund withdrawals until it is resolved,’ or so they said.
The issue? DL News, a crypto newspaper, had revealed two months earlier that Crypto4Winners was co-owned by Luc Schiltz. Schiltz was a Luxembourger found guilty in 2017 of defrauding victims of more than $1.5 million and sentenced to six years in prison, serving only two. Soon after his release, he co-founded the Crypto4Winners project.
So when the hack was announced, suspicions arose immediately. After the initial announcement post, Crypto4Winners went entirely silent. As soon as, if not earlier than March 12th, Crypto4Winners’ clients contacted lawyers and the police.
In the following days, it would be revealed that Crypto4Winners showed every sign of being a Ponzi scheme, which made thousands of victims for at least $100 million.
According to DL News, Luc Schiltz had co-founded Crypto4Winners but had kept his involvement hidden. The figurehead of Crypto4Winners was another Luxembourger, Adrien Castellani, its official CEO and founder. In truth, however, Castellani was only the co-founder of Crypto4Winners alongside Luc Schiltz.

Despite multiple questions about Luc Shiltz’s involvement in Crypto4Winners over the years, he never acknowledged him as either a co-founder or a general partner; instead, he barely recognized him as a consultant. In 2023, he promised to sever all relations between Crypto4Winners and himself by the end of that year, which he did not fulfill.

A little lie among many.
Such as the delirious returns they promised. They claimed a 377% return on customers’ Bitcoin deposits since 2019 and a 7% monthly average return of up to 20%, irrespective of the crypto market’s ups and downs, typical of a crypto Ponzi scheme.
They also claimed to be partners of Chainalysis and Ledger, which led both companies to publicly disavow their claims in 2022.
Crypto4Winners is incorporated in Sweden. When asked by the Swedish Companies Registration Office to provide annual reports of its accounts for 2021 and 2022 in 2023, it claimed that its status as a Trust Management Company did not require it to submit them, which was false. Even under the risk of liquidation or being declared invalid, the deadline came without them submitting the reports.
It would also be revealed that Crypto4Winners, which publicly appeared to be a Luxembourg-Swedish entity, was a complex structure spanning Dubai, Lithuania, Ireland, Sweden, and Luxembourg.
Worse, Crypto4Winners was, in fact, a shell company; investors’ funds were all transferred to an Irish company named “Big Wave Developments Limited.”
According to the Luxembourg newspaper Virgule, of the estimated $100 million in customers’ funds, not even $200,000 appeared to be left in Big Wave Developments Limited’s accounts.
The dumbfounding thing about this whole case is how its unraveling came about a very bizarre car crash accident that allegedly caused Luc Shiltz’s amnesia.
On March 5th, before dawn, Luc Shiltz crashed against a road guardrail, sending his car up a slope. He did not suffer any injuries from this accident; then, for reasons unknown, said the Luxembourg police, he walked into the highway where a bus crashed into him.
He did not suffer life-threatening injuries and was hospitalized in the orthopedic department.
However, he claims that the accident has caused him to suffer memory loss. Luc Shiltz has complete control over customer funds, which means he can no longer access the funds in cryptocurrency wallets and exchange accounts.
What stands out is that, according to the Virgule investigation and people who visited Luc Shiltz at the hospital days after the crash, there is room to doubt his amnesia.
Mario (fake name), a friend of Adrien Castellani, recounted to Virgule:
“He initially pretended to have amnesia and then told us that he would retrieve the USB keys from his parents, and that everything would return to business as usual…” (translated from French)
On that very day, Mario uncovered the shell nature of Crypto4Winners and Big Wave Developments Limited. Later, during a call on March 12th with Shiltz, Mario inquired about the mere $200,000 remaining in Big Wave Developments Limited’s account. Shiltz reassured him, explaining that it was to be expected since it represented only the funds in the hot wallet.
Despite his claimed amnesia, Luc Shiltz completely understands his identity and how his company operates. So one must ask, what exactly has he forgotten that prevents him from accessing the funds? Certainly not the seed phrases; it’s probably unheard of in crypto history for someone to rely solely on their memory, especially when $100 million is involved.
In his own words, he claimed that everything was with his parents and assured them that everything would soon return to normal. So, what’s the catch?
The answers to this question and all inquiries raised by this affair will hopefully be unveiled in a court of law.
On March 15th, the Luxembourg public prosecutor’s office announced an investigation into Crypto4Winners for fraud and money laundering charges. Two individuals have been charged and placed under custody.
One of the individuals is considered Luc Shiltz, and the other is Adrien Castellani.
According to the website created by the victims of Crypto4Winners, “Crypto4Victims,” no funds have been found during the investigation so far. In other words, Crypto4Winners could be a completely bankrupt Ponzi scheme. This is a nightmarish scenario for the victims as their hopes of recovering even 1/10th of their losses diminish by the day.

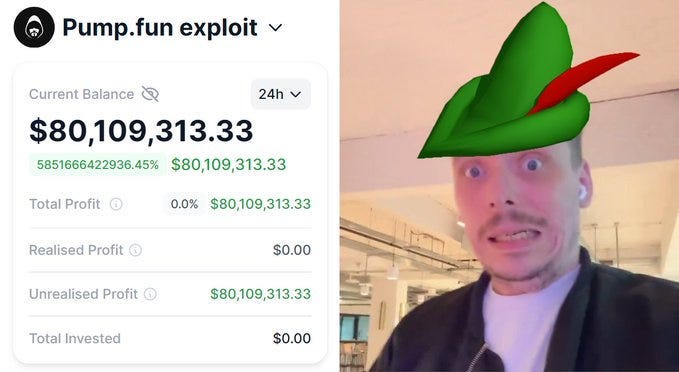
Pump.Fun Exploit: A Flopped $80 Million Revenge Plot?
Source: Twitter
On May 16th, 2024, Pump.fun, a Solana-based memecoin generator that has enjoyed immense success over the past months, lost $2 million to an attacker through a flash loan attack.
The attacker's identity was quickly revealed, as he took to Twitter within minutes of the attack to reveal his involvement!

In a rather chaotic thread, he explained that he was a disgruntled Pump.fun employee because his Pump.fun bosses were “the kind of horrible bosses that witness you wreck your hand, ask you what happened, u said the glass table gotchu, and they go ‘is that table ok?’ is not the type of ppl you want front n center as the face of blockchain.”
He then jumped into a Twitter space to share his woes and claimed that he ‘just kind of wanted to kill Pump.fun because it’s something to do… It’s inadvertently hurt people for a long’ reports Web3isgoingjustgreat.
His shenanigans didn’t stop there. In his original thread, he announced that he would airdrop $80 million (the amount he first assumed he would get to thieve) in stolen funds to random wallets. He did, as many people took to Twitter to share receiving the airdrop and thanking STACCoverflow for being a ‘Robinhood.’”
After the attack, Pump.fun shared that they were working with law enforcement on the attack, to which STACCoverflow replied, ‘Neener neener neener.’
‘Neener Neener Neener’ was somehow an apt reply, as STACCoverflow was already doxxed and was publicly known as Jarett Reginald Dunn. He knew the cops would come after he outed himself as the attacker and was politely waiting for them when they came to pick him up on May 17th in Covent Garden, London.
He was allegedly arrested and detained by law enforcement in London, held for 20 hours, and charged with “theft from the employer for $2 million with a conspiracy of another $80 million.” He was later released on bail under the condition that he return for an interview with the Criminal Investigation Department on August 16th and refrain from being involved with Pump.fun, he himself shared with crypto media Decrypt.
On June 4th, Dunn took to Twitter again to share his motivation behind the hack. His revenge stemmed from his Pump.fun bosses refusing to let him get a full-time side job at a different company even though his contract never stated he was forbidden to seek employment elsewhere. He was also stopped from earning the salary “new hires at Pump” received as he struggled to live correctly in London due to his inability to budget.

He also explained to Decrypt in great detail that he has been going through challenging times regarding his mental health over the past three years and is currently hospitalized for mental health concerns.
He also thinks he has the perfect “get out of jail” card, as he argued that the funds were stolen from Pump.fun customers and not Pump.fun itself, thus the Pump.fun case has no foundation.
On this, the future will reveal if his trump card was one or a dud.
In the meantime, although Dunn didn’t abscond with $80 million, he still accomplished his mission. Pump.fun’s reputation did take a hit, as a hack is never a good look when you’re in charge of millions of dollars.
Conclusion
These stories underscore the complexities and risks associated with the Web3 landscape. Nefture’s threat intelligence and protection work provides tools and knowledge to safeguard our crypto assets.
To be honest, I do not follow in-depth Web3 news, as it was overhyped a few years ago and is not bound to the cybersecurity world. But these 3 cases showed me that real money is made and hacked from the blockchain. Exploits are as significant as ransomware attacks. We are hearing more about the latter than the former, but cyber builders should pay attention.
Leave me a comment on what you think 👇
Laurent 💚
More from the Netfture Security Team. Here are two links: