◾️Resilience is the new black.
How resilience is transforming the cybersecurity landscape and why you should care.
Hello 👋🏼 Cyber Builders
The topic of the week is “Cyber Resilience.” I am sure you noted it is the new buzzword in our community. I am diving deep into why it makes sense and how it will shape the cybersecurity industry in the following years. Product Managers at vendors, Information Security officers at a midsize or large enterprises, and Cyber Builders must be ready for this new paradigm.
Before we dive in, I would like to ask you a favor. Share this post or the latest on “Secrets of Best Product Teams” with one of your colleagues or connection. Just forward the email! Please share it on LinkedIn, either. It will help me grow the readership.
If you have not already subscribed, please do so that you won’t miss the next post.
Cyber Loves Buzzwords
The security industry is known for its use of buzzwords and concepts. It's easy to fall into the trap of repeating the latest buzzword without genuinely understanding its implications.
In the security industry, there is a tendency to use fancy concepts and buzzwords to describe different aspects of the field. It's easy to get caught up in the hype and start using these terms without fully understanding their implications. While dropping a buzzword in a conversation may be impressive, it's essential to clearly understand its background and potential outcomes before implementing it.
As someone who used to be sometimes (oops!) guilty of this, I've learned to approach these concepts with care and to do my research before incorporating them into my work. This not only helps me to use these concepts effectively, but it also allows me to build better products that are indeed at the cutting edge of the industry.
As a cyber builder, I want to share my research with the community and get feedback to see if others are also investigating these concepts.
Resilience is the new black.
Let’s start looking at the definition of Resilience.
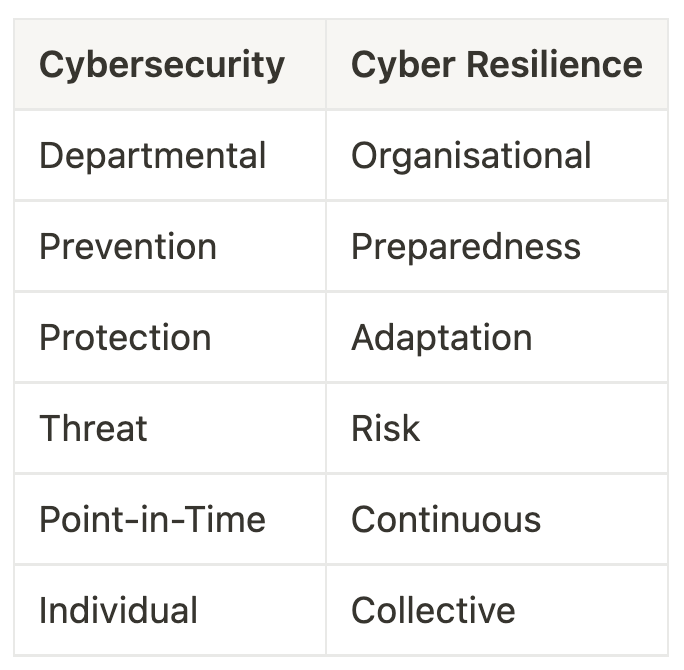
Resilience is the ability to anticipate, withstand, respond, and adapt to cyberattacks to minimize impact, expedite recovery, and emerge stronger. It is the ability to recover quickly from difficulties and to adapt to changing circumstances. In cybersecurity, resilience means being able to withstand and recover from cyber incidents while protecting digital assets and sensitive information.
It feels pretty obvious, isn’t it? You may wonder why I’m saying it’s the new black.
The fact that there is a growing awareness of cyber resilience is indicative of a shift in mindset when it comes to cyber security. People are beginning to recognize that there are no “cyber magic wands.” The reality is that cyber-attacks are becoming increasingly common, and there is no guarantee that any company will be able to avoid them altogether.
Let's take an analogy with the physical world. While it is true that we can take measures to protect ourselves, such as installing security cameras and alarms, the truth is that these measures need to be more foolproof. Just as burglars can still break into a home despite these precautions, cybercriminals constantly find new ways to breach networks and steal sensitive information. In many cases, they even demand ransom payments in exchange for returning stolen data.
This is not a problem that can be ignored or put off. It is something that every business must take seriously. Even if you are not an IT expert, it is still essential to understand the basics of cyber security and to take steps to implement best practices and protocols. This is not just an issue for engineers and technologists but requires a company-wide effort.
By proactively investing in cyber resilience, companies can better prepare themselves for future cyber-attacks. They anticipate helping their employees to resume working after the attack and supporting their customers from the devastating effects.
Implementing these measures may take time and resources, but the cost of doing nothing is much higher in the long run. The good news is that it starts to be in the mind of the highest company governance: the boards.
Image from OpenAI DALL-E : “A resilient and safe man facing a sea in a futuristic city”
The board needs to shift focus.
A well-written article from the Harvard Business Review argues that boards of directors often view cybersecurity as a technical issue when it has become a critical organizational and strategic imperative. Rather than simply focusing on protection from cyber threats, boards would be better served by prioritizing resilience in the face of potential attacks.
A quote from the article:
Notwithstanding the high perceived risk, our survey found that 76% of board members believe they have invested adequately in cyber protection. Furthermore, 87% expect their cybersecurity budgets to grow in the next 12 months.
However, their investments may not be in the right areas. In a typical board meeting, the cybersecurity presentations usually cover threats and the actions/technologies the company is implementing to protect against them.
As cybersecurity becomes more critical, boards must improve their oversight. The problem is the lack of communication between board members and chief information security officers (CISOs) and the focus on protection instead of resilience. To improve, boards must build stronger relationships with CISOs, focus on resilience as the primary goal, bring cybersecurity expertise into the boardroom, and prioritize it through regular discussions.
By doing so, boards can better understand their organization's cybersecurity risks and develop strategies to manage them and maintain resilience. Building a culture of cybersecurity can help companies withstand and recover from cyber incidents while protecting digital assets and sensitive information. Cybersecurity is not just technical expertise but critical to business strategy and risk management.
CEOs get it
Enterprise CEOs are increasingly aware of the importance of cybersecurity. An exciting talk occurred at RSAC 2023, given by Manuel Hepfer, from Istari and MIT Sloan, about why cybersecurity is a strategic asset for enterprises.
ISTARI is the Temasek Cybersecurity Platform. Temasek, headquartered in Singapore, is one of the most prominent investors in the world. ISTARI groups its cyber investments and security practices.
Hepfer's talk started with a ransomware attack story on a multi-billion company. The speaker shares the CEO's perspective, and the story is one of the motivating factors for the research. Insightful quotes of that CEO are:
Before the attack, it was impossible to think anything could put us out of business. This was the first time in my career that I had no intuitive idea of how to move forward.
ISTARI runs a research project to explore how CEOs approach cybersecurity. The project aims to answer the following questions: Are there differences in approach between CEOs who have experienced a significant breach and those who have yet to? Are the current cybersecurity frameworks sufficient for CEOs?
They had 37 CEO interviews with average revenue of $12bn, 40k employees, and an average tenure of 8 years. Nine CEOs from the USA and nine CEOs experienced an attack. The companies were from top banks in the EU/USA, telcos, and retailers, with 15 CEOs from Europe and 13 from APAC.
💡 They ended up with one great learning: “Resilience” is more important than “Security.”
One key lesson learned is that "resilience" is ultimately more important than "security" for this group. ISTARI defines cyber resilience as “the ability to anticipate, withstand, respond, and adapt to cyberattacks to minimize impact, expedite recovery, and emerge stronger.”
Effective risk management is one of the most critical aspects for a CEO of a large organization. A CEO must constantly be aware of potential threats to protect their organization from harm. However, cybersecurity is not just about prevention. It should also focus on building resilience. Resilience means that an organization can quickly respond to threats and quickly recover from any damage that may have occurred. Cybersecurity must focus on prevention, preparation, response, and continuous learning to achieve resilience. This includes conducting regular risk assessments, developing comprehensive incident response plans, training employees on cybersecurity best practices, and constantly reviewing and updating cybersecurity policies and procedures. By building a culture of resilience, organizations can better protect themselves against cyber threats and ensure their long-term success.
Security and Resilience - Extracted from ISTARI presentation
There is a lot of valuable information in the ISTARI report, which you can download by clicking on the link (https://bit.ly/CEOResearch). I highly recommend thoroughly reading the report, as it will provide you with a deeper understanding of the cyber resilience matter and help you make more informed decisions moving forward.
I highlight some of their key recommendations below and extract redacted quotes from the interviewed CEOs.
Be co-responsible, not just accountable for cyber resilience.
I am what I call co-responsible. If you asked our CISO whether he feels responsible for cybersecurity, he would say yes. But I think it’s vital that we as leaders also feel responsible, not just accountable. You cannot delegate this to experts. If you don't feel responsible, you don't participate and be involved enough and then. Indeed, I think this will weaken our resilience.”
Embrace the preparedness paradox.
It quickly dawned on us how ill-prepared we were and how little we knew about the real risks of being hit by something like that. We did not understand how severe the risk could be. We couldn’t even imagine it.
Move from blind trust to informed trust.
You've got to be curious and lead and ask questions because technology is constantly changing. You need a lot of humility. You've got to assume somebody's going to get in, and then you've got to figure out what am I going to do once that happens. So you've got to be aware, you've got to ask questions, but you've also got to have the humility to keep asking to learn.
Adapt your communication styles to regulate stakeholders: facing a cyberattack is a major emotional stress for a CEO
I feel obligated to our stakeholders because they rely on me to ensure that we take this seriously in the company and that cyber is an integral part of our strategy. So I feel the weight of responsibility to take a visible leadership role in making all our stakeholders see this importance.
Let me summarize a brief history of cybersecurity concepts and how resilience might help ignite new products and positions.
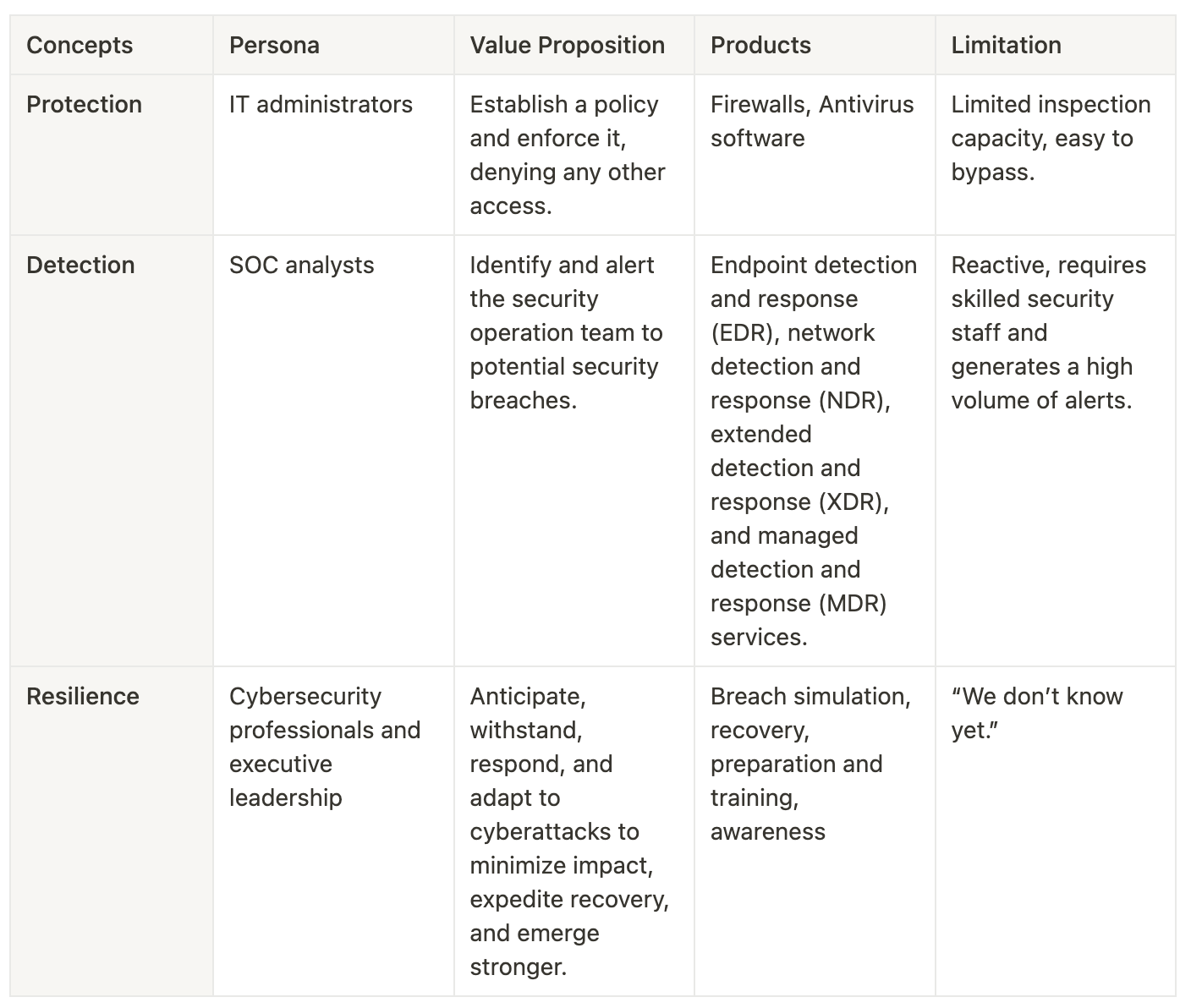
Cybersecurity Concepts - Protection
In the early days of cybersecurity, the primary focus was on protection. At the time, information security was a relatively new field, and the concept of cybersecurity had not yet been coined. Back then, the main concern was keeping the network safe from malicious hackers, seen as a threat lurking outside the perimeter.
The first products were developed for the IT administrators to ensure the company's protection. They defined the two main categories in IT security today: network-based products and endpoint-based products.
From a network perspective, the primary need was to enforce the perimeter and prevent unauthorized access outside the network. The first firewalls were created, moving from stateless connection tracking that only authorized IP addresses to stateful connection tracking. Initially, users were IT staff who opened ports to allow applications to work with their flows through the firewall. Over time, companies added VPNs for data encryption and gateway authentication, DPI for traffic inspection, and many more features.
This sector has grown significantly over the last 20 years. If you combine Network Firewall, Network Detection and Response, IDPS, Network Access Control, and Zero Trust Access, you will have a 16 billion dollar market in 2022 (Source: Gartner).
Another common form of protection is antivirus software. These programs are typically installed on laptops, workstations, and servers. Initially, they scanned all the files on the hard drive, but their capabilities have since expanded to include real-time inspection of file access and network connections.
The value proposition of the protection product is straightforward: you are establishing a policy, and I will enforce it, denying any other access. But over time, we learned their limitations.
It is very easy to bypass a firewall: as these appliances are optimized for network speed, their inspection capacity is limited, and it is easy to obfuscate a malicious payload. Moreover, with mobile devices moving in and out of the network, it is hard to think that the firewall would see all the communications.
They remain a de facto standard of any network architecture, as in the physical space, we are implementing doors and locks. A well-known mechanism serves as a first barrier.
Cybersecurity Concepts - Detection
With the limitations of protection products becoming more apparent, the industry began to focus on detection. Detection-based products seek to identify and alert IT staff to potential security breaches. These products include endpoint detection and response (EDR), network detection and response (NDR), extended detection and response (XDR), and managed detection and response (MDR) services.
Detection-based products are designed to identify malicious activity that has already penetrated your network. They are also designed to reduce the attacker's time within your network before detection. The shorter it is, the less damage an attacker can do.
EDR and XDR solutions can monitor endpoints, network traffic, and cloud infrastructure to identify potential security threats. The security operations team manages EDR and XDR, often grouped within the SOC (Security Operation Center). They are high-value experts, looking at alarms and investigating weak signals from their tools.
MDR services provide a more hands-on approach to threat detection and response. These services typically include 24/7 monitoring, threat hunting, and incident response. MDR services can be particularly useful for small and mid-sized organizations that may not have the resources to manage their security operations in-house.
While detection-based products have numerous advantages, they also have their limitations. One of the most significant limitations is that they are reactive rather than proactive. That is, they only detect threats that have already breached your network. Additionally, detection-based products require skilled IT staff to manage them effectively. Finally, these solutions can generate a high volume of alerts, creating alert fatigue and making it difficult to distinguish between genuine threats and false positives.
To learn more about Detection, read The Six Pillars of CyberSecurity Platforms.
Cybersecurity Concepts - Resilience
Nowadays, Resilience is the new trending topic. You need some protection; you need some detection and response. But you will eventually be breached and must prepare to recover and remediate. So you need to be more resilient.
Cyber Builders has built teams for network and security architecture and Security Operation Centers over time. As we move towards a resilience-first approach, what kind of team should they build?
In addition, Cyber Builders has developed products such as firewalls, EDR, and SIEM. What are the products and technologies that will be at the forefront in the minds of enterprises prioritizing resilience?
I don't know if we already know that answer. There are many options, and many others will emerge. Let’s brainstorm:
Awareness. Many startups and vendors offer awareness products, from employee security training to phishing simulation.
Adversary Simulation. Innovative technologies have been created to simulate cybercriminals within a network and show how they would move laterally exfiltrate data or hack systems. These simulation tools either use a 100% “in silicon” approach with a model-driven approach to your IT system or a hybrid approach with some scanning of live systems and some model.
Recovery. How are you able to recover from a cyber attack? I guess backups and restore systems are
Preparation and Training. Crisis management solutions and table tops exercises help the teams to get ready. I expect the interest in these products to grow over time.
Last but not least, on the organizational side of things, it is crucial that the CEO takes co-responsibility for the company's information security. This means that the CEO should support the infosec team and actively ensure the company's information is secure. To do this, the CEO can help communicate between the infosec team and the rest of the company, ensuring everyone is on the same page regarding security measures and protocols. Additionally, the CEO can work closely with the infosec team to develop and implement effective infosec strategies that align with the organization's overall goals and objectives.
Conclusion
Let me synthesize this essay within one table:
Don’t hesitate to transfer this email to your friends. Click the button below or just forward the email. 😁
If you enjoyed this edition, please give it a little love by clicking on the heart. Your response will help me assess how much you appreciate (or don't) my writing. And lastly, don't forget that I'm always here to reply to your emails! If you have any comments or feedback, just hit the reply button, and your message will reach my inbox.
Have a wonderful day.
Laurent. ❤️