RSAC2023 Wrap Up - Unraveling the Convergence of AI and Platforms in Cybersecurity
Discover how artificial intelligence and platform-based solutions shape cybersecurity at the world's leading conference. Plus personal views of RSAC2023!
RSA Conference 2023 concluded on Thursday. It was a busy week for me, with a dozen talks, vendor conversations at their booths, and meetings with old connections. It was an excellent opportunity to have in-depth conversations with entrepreneurs I advise and startups I am an early investor.
This post will cover the conference's strengths, significant themes, and takeaways. I will briefly explain each. On some topics, I plan to dive deeper into a dedicated post. If you missed it, check out last week's post on how Generative AI (GPT-4) can easily pass the Certified Ethical Hacker exam.
It’s always about People.
First of all, one of the significant strengths of this conference is its excellent attendance and the diverse cybersecurity community it brings together. With over 40,000 cybersecurity professionals, vendors, sales and product managers, CISOs, and representatives from the public and private sectors, this conference truly encompasses all facets of cybersecurity.
Furthermore, the conference provides ample opportunities for attendees to establish new connections and expand their professional networks. Attendees can engage in various networking events, such as meet-and-greets and social gatherings, where they can mingle with colleagues, reconnect with old acquaintances, and even meet new people they have only previously interacted with electronically.
It is interesting to note that sometimes, even in this age of advanced technology, traveling to San Francisco is necessary to meet European contacts. This paradox further emphasizes the value of in-person interactions and highlights the importance of attending conferences like this one to foster new relationships and strengthen existing ones.
With more than 300 conferences, it can be challenging to attend all of them. Therefore, my program is focused on seizing opportunities to dive deep into some topics, listening to large corporations' visions during keynotes, or catching up with the big themes of the conferences. I include some of its central themes below.
RSAC is the only place you can find Cyber and AI ads at bus stops!
The age of the platforms.
A significant factor in the cybersecurity industry is transitioning from providing top-notch products to becoming a platform provider. This move responds to customers who express fatigue from using disconnected solutions that only focus on specific security aspects such as emails, IoT, web, cloud, etc. Security organizations have limited budgets and resources and cannot afford to switch between hundreds of point products.
This marks the age of the platforms. A platform assembles several features under the same user experience, with unified pricing and improved productivity for security users. Cybersecurity is a data-driven sector; the more data you have within a platform, the more value you can expect. Imagine seeing a strange behavior from an EDR (Endpoint) log; using the convenient feature, you can expect to “pivot” to another data stream - for example, the outbound web access log - to understand if a C2 server controls the endpoint. In that use case, first, you get a better way to analyze multiple events (”data”) streams, and it is far more manageable as you don't spend time switching from various products with different UX.
There are at least two streams of “platform” vendors. During the RSAC, all major cybersecurity players pitched how their platform is superior to others. Incumbent security players, such as Cisco, Palo Alto, and Trellix (formerly FireEye and McAfee Enterprise), are positioning their platform as an XDR, able to connect and orchestrate multiple points products, including their existing network, endpoint, or applicative solutions. Then comes the cloud actors such as AWS, Microsoft, and Google. They have large computing and storage capacities and are eager to use them with the right software.
I plan to analyze these trends in detail in the upcoming newsletter.
AI improves productivity…
AI was a hot topic during the conference. All vendors claimed that they had turbocharged their product's capacity with some AI. Some of their announcements were vague and fluffy, others more exciting.
However, Microsoft and Google demonstrated how generative AI could help security analysts understand and triage the value of alerts they receive daily. Their security chatbots are impressive, as they adapt to the context and questions asked by the user. Both are chatbots targeted for security operations and SOC teams. These chat interfaces are open-ended, making them very accessible to everyone.
I agree with AI's vision to improve the productivity of less skilled staff members. If you are new to a job, there is often a steep learning curve when using technical tools like logging systems or query languages like Splunk or Microsoft KQL. This is where computers can be beneficial. Algorithms don't judge you, so you can ask any question without fear of being judged. If you ask a "silly" question, an AI will provide examples and guidelines to help you better understand.
Another example of such a vision is coming from Gitlab. GitLab has recently launched an ingenious feature set to improve how teams tackle vulnerabilities in their codebase. The tool merges vulnerability information with code insights to provide valuable context, exploitation details, and even example fixes. Early testing of this feature has significantly reduced the time to fix vulnerabilities. With AI-powered vulnerability recommendations, developers can fix security loopholes more efficiently than ever.
… and brings new issues
Several conferences discussed the limits of AI technologies and how to evaluate them. I appreciated the tone of many talks where speakers prevented themselves from doing fear-mongering related to AI and focused more on the practical implications of AI.
Many talks included the “ChatGPT and Security” topic. Whether ChatGPT poses a man vs. machine or machine vs. machine problem is an exciting concern. On the one hand, ChatGPT's advanced capabilities may outperform human cybersecurity experts, leading to a man vs. machine dilemma. Balancing human expertise and AI-driven automation is essential for optimal security. On the other hand, AI technologies may cause a machine vs. machine issue in cybersecurity, with AI-powered attack and defense mechanisms racing against each other. This raises questions about the future of cybersecurity.
Criminal organizations will use the power of generative AI to automate a personalized stream of spear phishing emails and messages. With a few sentences on a person - extracted, for example, from their LinkedIn profile - GenAI technologies can build a well-written email. For instance, ChatGPT can create convincing and personalized phishing emails that are harder to detect in multiple languages. It can analyze or generate code to detect or exploit vulnerabilities. It can also manipulate employees by forging conversations on collaboration tools like Slack and Teams.
Hackers can bypass safeguards. An example is "DAN" (Do Anything Now) (see live research here), which allows ChatGPT to bypass its moral and ethical limitations. In that case, ChatGPT generated code that could hide malicious activity from Windows Defender when asked to do. Although the code did not run perfectly, it provided a starting point for potential attackers, making it easier for them to create a functional bypass.
It will be necessary to utilize technology to monitor and analyze the actions of LLMs and Generative AI. On this track, one notable software release during RSAC week was NVIDIA's open-source technology for implementing LLM's safeguards (link). We are not yet done hearing about AI and Cybersecurity. I plan to continue to work on this topic and do my research. In that sense, check out how GPT-4 can pass the Certified Hacker Exam.
No more honeymoon for MFA
There has been a shift in the security community, and MFA, which was once considered the ultimate authentication method, is no longer enough to protect against sophisticated attacks.
Jason Haddix, the former Head of Security and Risk Management of Ubisoft, the video games company, gave an excellent talk. He detailed the attack he had to respond to it. His speech was interesting as he demonstrated how far the attackers invested in hacking authentication systems.
Adversaries have used cookies to gain unauthorized access to 0365 accounts. They also exploit fresh cookie sessions to log in via Slack Web. Using this technique, they did not require to bypass the existing authentication scheme. They need a credentials stealer installed on the endpoint - in the detailed case, a BYOD device - and can leverage long-living cookie sessions. Indeed, Slack or another tool set up within the user’s web browser cookies that never expire to ease users’ reconnection.
In other cases, attackers use stolen credentials to bombard users with repeated 2FA prompts, and if the user clicks just to get rid of the phone prompt, the attackers win. As a last resort, they call the user and trick them into clicking the prompt by claiming to be from security or IT. Their main objective is to gain VPN access.
Lastly, attackers also used Adversary-in-the-middle (AiTM)
AiTM phishing has been available for several years and is still the most common type of attack. The AiTM phishing campaign has attempted to target over 10,000 organizations since September 2021, according to Microsoft MSTIC.
Traditional credential phishing sites collect the user's credentials but do not complete the authentication process. With MFA enabled, attackers cannot log in to the account with the stolen credentials.
AiTM phishing attacks bypass MFA by completing the authentication process and capturing the token. Three widely known open-source AiTM phishing kits exist Evilginx2, Muraena, and Modlishka. AiTM works as a proxy between the victim and the target site. Every modern web service implements a session with a user after successful authentication, so re-authentication is unnecessary for every new page. The session functionality is part of the session cookie the authentication services provide. The web server with the AiTM phishing kit proxies HTTP packets, making the phishing site identical to the original website. The URL is the only visible difference between the phishing and Microsoft sign-in sites.
MFA is still a very important Defense in Depth measure. It is mandatory in many security policies because it decreases the likelihood of credential steals and makes attacks more complex. Still, AiTM and other adversaries’ tactics show that it is no more the panacea of authentication. I think new IAM (Identity and Authentication Management) features are needed to add more detection within these systems to detect earlier phishing schemes.
Cryptography is the mother of all cybersecurity technologies.
Cryptography, as the backbone of all cyber technology, has played a crucial role in securing sensitive data and ensuring the confidentiality of communication. The RSA Conference (RSAC) provides a unique opportunity to hear from the pioneers of cryptography who made it happen in the 80s and 90s. The conference features a panel of renowned cryptographers, including Adi Shamir, Whit Diffie, and Paul Kocher, who have made significant contributions to the field. In recognition of his significant contributions, Kocher was honored with the RSA Conference 2023 Award for Excellence in the Field of Mathematics.
Attending the cryptographer panel is an enriching experience for me as I get to listen to the stories and insights of these brilliant minds and their fellow cryptographers. One of the highlights of this year's panel was the discussion on the concepts of public key cryptography, which was invented by Clifford Cocks, former head of cryptography at UK GCHQ, nearly three years before Diffie and Hellman. The panelists also discussed the field's challenges and opportunities and the latest developments and trends.
As a security practitioner, I feel privileged to work in a field where the people who invented the core algorithms are still active and contributing to advancing the field. It is a testament to the rapid pace of technological development and the importance of cryptography in safeguarding our digital lives. This experience reminds me that we are a very young industry with much to discover and explore.
Overall a very diverse conference
I've been hearing a lot of complaints about vendors playing too much lousy marketing (and replaying it!). The expo was huge; some booths even had speakers for short briefings, games to win gifts, and giveaways. Each booth had a prominent tagline filled with buzzwords. But let's face it; this was a vendor expo with people selling their products and services. They should not be shy and not even try to make their brand visible and attractive. The visitors get very used to the sales mood of the expo very quickly.
But I don’t think that the expo is the core of RSAC. RSAC monetizes using vendors paying fees to be part of the expo, but the core of RSAC is the conferences.
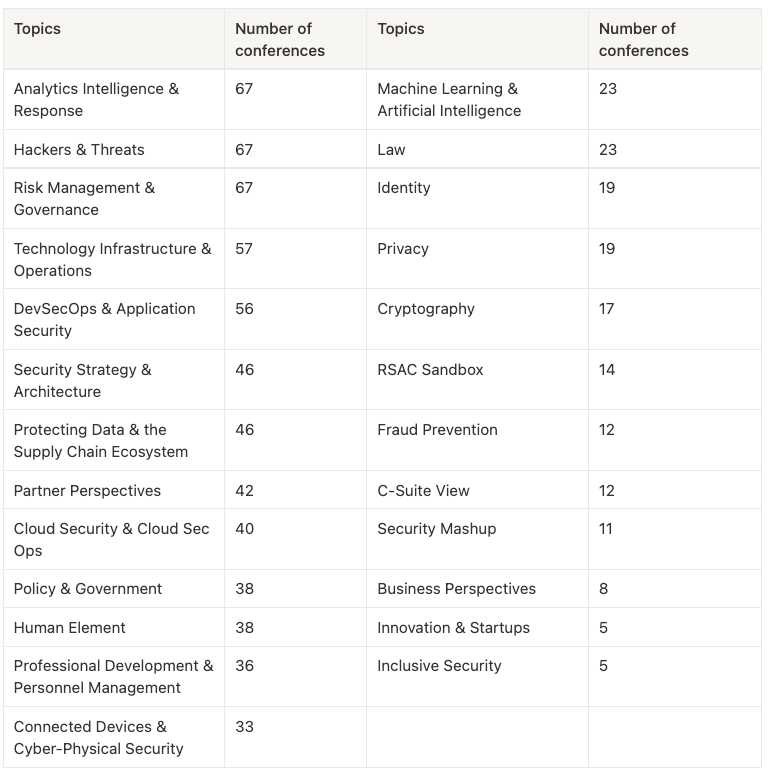
Conferences are very diverse; I provide an overview of the topics and the number of conferences in the table below.
All sessions are also classified regarding how far they go in their topics.
The RSA Conference's true strength lies in its broad range of topics. As a security professional, you must stay informed on various subjects, from law and cryptography to cyber-physical systems and cybersecurity governance. The RSA Conference provides a unique opportunity to catch up on all these topics from recognized experts in just one week. Threat Intelligence and the latest exploitation or hacking techniques are usual topics. This year, we can note the significant number of talks dedicated to the “Shift Left” mindset or DevSecOps.
While not a hacker conference, the RSA Conference offers the chance to spend an hour speaking with experts on migrating to post-quantum cryptographic algorithms, followed by a talk on the best ways to present your security activities to the CEO. Most talks are not commercial or sell a product. The sponsored talk by a vendor is tagged as is, and as a visitor, you know what to expect.
Conclusion
I cannot conclude this post without mentioning the shocking and worrisome homeless situation in downtown San Francisco. I was not since years in downtown San Francisco, but I did not remember a situation like this. I spent many hours walking through the streets of the city, and the situation of the very poor and how drugs and alcohol impact them is painful to see. Within the same place, seeing luxury or self-driving cars, the worldwide cybersecurity community, and the homeless is quite a paradox.
We won’t be “Stronger Together” at RSAC if the city officials are not helping these people.
Please stay connected with Cyber Builders by subscribing to Substack. One email per week.





Great summary of the conference
Big opportunities ahead