SMB Cybersecurity Success: The 5 Must-Haves
Unveiling Essential, Often-Overlooked Keys to SMB Cybersecurity Success
Hi there👋
Thanks for the new weekly edition of Cyber Builders. I am closing my July 2023 series on the cybersecurity SMB market this week. I want to share five must-haves that any Cyber Builder will implement to succeed. If you missed the first parts, follow the links below:
This post closes the series on 4/4 🎉
Before we dive in, please ensure you will continue receiving my once-a-week email. Many of you have not seen the posts anymore because they fall into your spam folder. Please make sure it is not happening.
Could you move this email into your main Inbox? 📥
If you’re using Gmail, please move this email from promotions (or any other tab) to Primary for better visibility. The **promotions tab is where most newsletters go to die.
If you’re using Apple Mail, please select my email address and then select “Add to VIPs.” This will ensure you get the emails.
Thanks a lot 🙏
Back in the day, creating cybersecurity software for small businesses…
I used to work for software companies that sold security appliances to SMBs and mid-market organizations (link to the first post). When I joined as a young engineer, I must admit that I thought the better the product, the better the sales. I used to believe the company's success was tied to the richness of the product features. I even had confirmation bias working for me: every time I talked to sales, they would tell me stories of lost deals due to missing product features.
"Hey Laurent, is your team ready to ship Feature XYZ? If we can't commit to it ASAP, we are 'dead' at customer ABC."
If you've been a cybersecurity professional for some time, you've probably heard these sentences before. Unfortunately, the cybersecurity vendors’ world is still too often driven by the number of features rather than accuracy. You'll hear things like "Even if you don't need it now, you should pick my product as a future-proof option" from vendors.
Note that a missing feature could be an issue for the end user. For instance, a missing third-party integration will reduce the overall value of a detection tool that cannot send alerts or any practical aspects needed by security practitioners using your product.
However, most of the time, ensuring the success of your business requires more than just product features. This is especially true when targeting SMBs.
There are five must-haves for SMB cybersecurity products and services.
A strong channel - resellers and partners
A training and certification program
An always accurate documentation
A knowledgeable marketing strategy
A state-of-the-art set of 3rd party integration and partnerships
1st - A strong channel - resellers and partners
Founders focus on the product in their first venture, while second-time founders focus on distribution.
This adage is often repeated in the investor and entrepreneur community and is particularly relevant in cybersecurity. Many great products will never succeed because the founders of their companies need to understand that their role is not only to create technology but also to create a company with employees and the ability to distribute these products.
Big players rely heavily on their ecosystem to distribute their products in cybersecurity. It is widespread to see indirect models, where the final sales transaction is carried out by a reseller who bills the customer and is billed by the software vendor. This is the only solution for scaling commercial activities on a global level quickly and efficiently.
This model requires significant investment in sales and marketing and takes a long time to set up due to the need to grow partner programs, train partners, and teach them how to sell. Building a network of resellers is a time-consuming process that involves recruiting, training, providing arguments, and hoping that their local influence will produce results. Publishers are often present for the first sales with their partners.
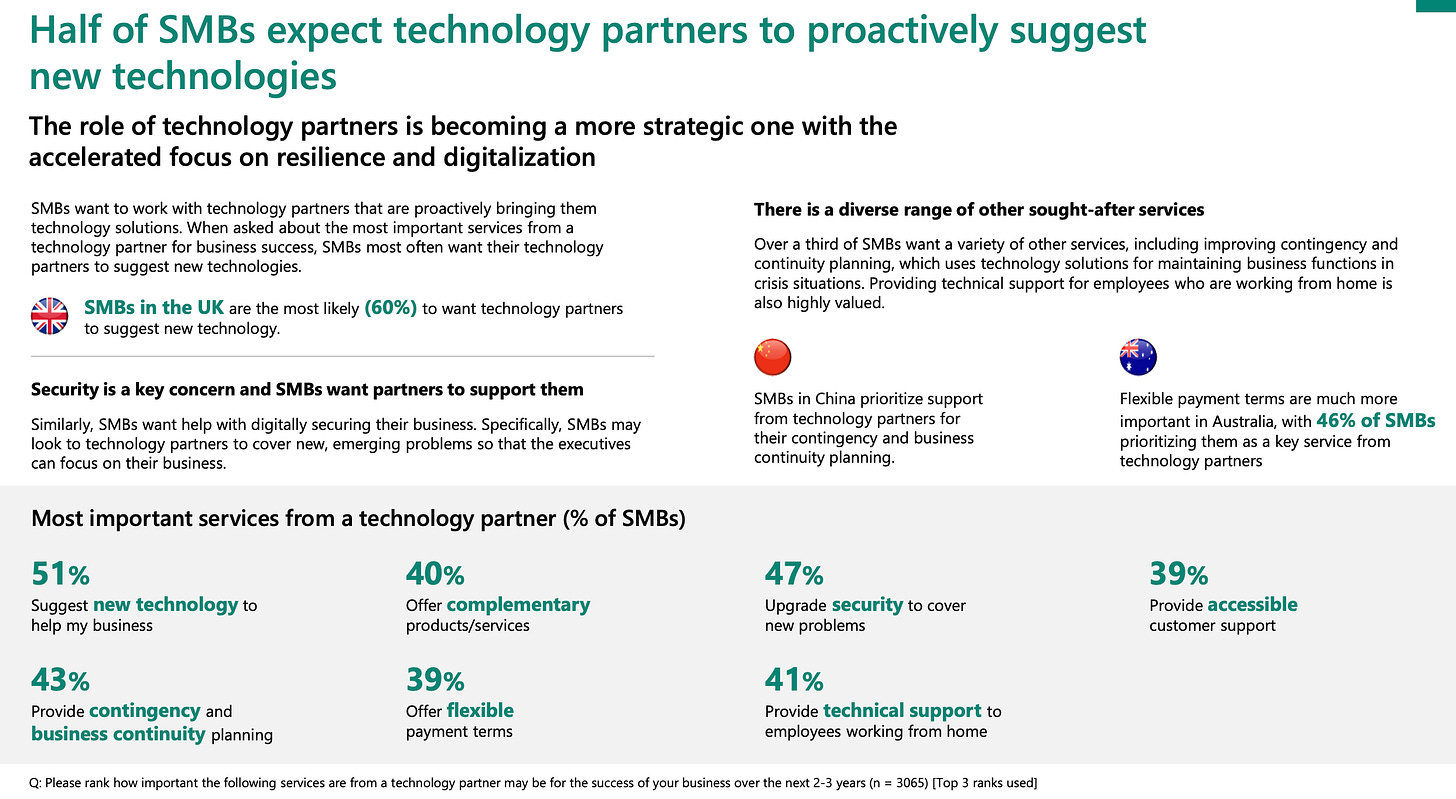
If it seems a waste of time and effort for you, but you think you can still target SMB, think twice. Partners have a tremendous power of recommendation. A recent Microsoft study showed that in the SMB market, more than half of companies trust their traditional IT service providers for IT or cybersecurity product choices. With such an impact, these providers and these partners are an imperative distribution channel.
For Cyber Builders, the role of these partners are:
Help to sell by recommending SMB owners and IT decision-makers your product.
Add up integration and configuration service to ease onboarding.
Provide local customer support and act as a one-stop shop to help SMB IT staff.
As discussed in the previous posts, SMB and mid-market companies have few IT personnel. They must rely on third parties to operate their systems.
Lastly, we see a new go-to-market in cybersecurity: Product Led Growth. I will cover it in a subsequent newsletter, but I don’t think it fully replaces the role of such reseller programs. Strong partners around your company are material in a market with skills and resource scarcity.
2nd - Training and Certification programs
Whether it comes to having users and partners around a product, implementing a user training and certification program is crucial. A technological solution, such as software, is undoubtedly complex to use to its full potential. Therefore, assisting in the first hours of use is essential, enabling quick training and implementing best practices.
Traditionally, this involved sending employees to the software vendor’s premises for two to four days to attend training and ultimately take a certification exam. By doing so, vendors built a community of experienced users. Their certification label gained value as the product became increasingly used and recognized. Cisco CCNA is a great example of a well-executed certification program with market recognition, helping professionals’ careers.
Nowadays, these practices have been modernized. It is effortless to set up a series of initial training courses through videos on YouTube, combined with additional modules delivered remotely with a video conferencing tool. In-person training remains an option for in-depth training, using rare resources such as testing equipment or attack simulations like cyber ranges. This approach also strengthens the links between certified professionals and publishers.

3rd - Always accurate documentation
Having precise, easy-to-consult, and always up-to-date documentation is mandatory.
Documentation and software users are, first and foremost, a matter of trust. At some point, we have all searched through a software's documentation.
😁 If the experience were good, we would likely return to it the next time we face a difficulty.
🤬 If it is wrong, we often rely on our first experience and do not go back to read the f**** manual.
Good documentation should provide three entry points.
The first is the getting started guide for new users. What should I do to start and, within an hour, already have the essential value of the software in my hands by creating my first elements in this new software? Good documentation must provide help in getting started.
Users likely want to access documentation through use cases. For example, with cybersecurity software, users may need to create a report to comply with specific regulations. We can document how to configure the software to detect specific threats. For each everyday use case the user may encounter, precise documentation allows them to respond and implement it effectively. It is relatively simple if you are still deciding which use cases to start with: look at the most asked questions or ask technical sales.
Unfortunately, the last approach is often the first done, which involves describing the user interface and explaining the software's various functions. With the recent emphasis on user experience (UX), this step can be redundant since the on-screen elements are often self-explanatory. However, this approach doesn't necessarily guide the user through specific use cases and can hinder their ability to use the software effectively.
4th - Marketing
The fourth criterion is to have effective marketing. Be careful, not marketing filled with keywords, buzzwords, and often bombastic announcements that are unpalatable, but marketing that will allow you to raise the level of understanding of the various stakeholders around the company.
What I mean by that is, for example, having a series of articles on your website or webinars that clearly explain what needs to be protected against and what your clients encounter with the most common security problems. This “smart” marketing that seeks to teach your users, clients, and partners knowledge will position your business as an expert.
The marketing strategy should replace the role of consultants by clearly explaining and defining the problem, putting it in perspective with the reality of a small and medium-sized business. This approach can be as convincing as hiring a consultant to perform this type of analysis, evangelization, and continuing education for employees of large companies, making your business appear as an expert and raising the average level of knowledge around you.
5th - Third-party integration
The fifth criterion is integration with third parties. Indeed, a security product is never alone in an information system. It is always used with other software, and your users, whether large accounts or SMBs, will always need to see their software integrated with your security product.
So ask yourself whether your reports are exportable in Microsoft Office tools; if you can easily integrate with your clients' firewall or antivirus to provide additional value. Consider how you can automate by leveraging knowledge within your client's information system. Finally, connect to chat systems like Slack or Microsoft Teams that allow you to reach the user where they spend most of their time exchanging and interacting.
Integrating with certain parties can significantly enhance the value proposition of your solution. This can be achieved by offering additional features or services that complement your product, increasing its appeal to potential clients. Such integrations can also help build trust and loyalty with your existing user base by demonstrating your commitment to their needs and preferences. By making it more difficult for clients to disconnect from your solution, you are effectively increasing the switching costs and creating a barrier to entry for your competitors. Ultimately, this can result in a more robust and sustainable business model that delivers long-term value for all stakeholders.
And the 6th and “bonus” one … a good product!
The last item you should consider is the product, but only in addition to addressing the points mentioned above. For SMBs, the product must be easy to install and use. It should be set up within an hour, maximum, without requiring several days of consulting.
It is also crucial that all needed information be accessible within one or two clicks. This includes the data the user needs to see each time he logins and all its general usage scenarios. The interface should be intuitive, instant, and easy to access. This is key to ensuring user adoption and satisfaction.
Finally, your solution should follow an all-in-one logic. While a cybersecurity manager in a large enterprise may be able to obtain an additional budget to fill a small functional gap in a solution, an SMB client does not have this luxury. They are looking for the maximum value for their budget, not necessarily sophistication. They need helpful something that provides a first level of protection, detection, or resilience, all within a defined budget. This all-in-one logic is crucial when addressing the SMB market.
Conclusion
Regarding cybersecurity products and services for small and medium businesses, several must-haves are essential for success. These include a strong channel of resellers and partners, training and certification programs, consistently accurate documentation, a knowledgeable marketing strategy, and a state-of-the-art set of 3rd party integrations and partnerships. By focusing on these critical areas, Cyber Builders can create effective solutions that meet the unique needs of the SMB market.
Thanks for reading the series. Please share your thoughts in the comments below.
If you like it, use the little. ❤️ on Substack to send me encouragement. Don’t forget to recommend Cyber Builders to your colleagues, fellow entrepreneurs, product managers, or engineers and earn a reward!
I look forward to seeing you next week.
Best