Would Cybersecurity Requirements Change The Business Model of Devices Manufacturers?
Exploring the implications of the EU Cyber Resilience Act, the European version of “Shift Left Security.”
Hello Cyber Builders 🙋🏻♂️
The latest cybersecurity requirements, for example, from the EU Cyber Resilience Act, are prompting a significant shift in the business models of many manufacturers.
The traditional 'build once and sell multiple times' approach will evolve as more software is integrated into products. This transformation requires manufacturers to take on a more active role in product lifecycle management, necessitating regular software updates and heightened security measures. This paradigm shift from a one-time transaction to an ongoing relationship between manufacturers and consumers. Continuous product support, regular updates, and consistent vulnerability management characterize it.
This new business model would demand a more proactive and engaged approach. Would it be confirmed in the following years? It is exciting for cybersecurity experts to push for a shift left approach, but would the vendors support the cost?
This post is part of a series:
🔗 The Future of Cybersecurity: Everyone is a Software Producer. As software takes command, a new cybersecurity battlefield - software product security and its supply chain
🔗 Securing Software Supply Chains Start by Empathy. Exploring the Operational Triad of Software Product Security - Developers, Business Teams, and Product Security Officers
🔗 Understanding the Impact of the EU Certification Scheme on Cyber Builders
The new EU Certification Scheme is a nice first move but raises many questions about cost, complexity, and communication.
🔗 Building Secure Software: Top 11 Best Practices in Cybersecurity From Threat Modelling to Fuzzing: All You Need to Know about Software Security
Unsecured Product Impact on Society - The Mirai botnet story
As software continues to permeate every aspect of our lives, from professional spaces to personal living, it is crucial to ensure its security. Today, software doesn't just belong to tech companies; it is integral to businesses across various sectors, from hospitality to retail.
When you buy a product today, it usually comes embedded with software to enhance its functionality. However, this software is often overlooked regarding updates and security checks.
This lack of attention to embedded software security creates a vast 'security debt,’ posing a significant risk on a colossal scale.
The Mirai attack of 2016 is a well-known example of the risks associated with unsecured products. Hackers targeted tens of thousands of individuals connected through the Internet. Through primary video surveillance cameras, typically purchased for a modest price, people could view the footage of their homes, businesses, or stores. These cameras had been in place for months or years, functioning flawlessly. However, no one had examined their security settings or considered the need to secure them.
Extract from: https://www.imperva.com/blog/how-to-identify-a-mirai-style-ddos-attack/
The hackers decided to infect these cameras, using them to search for and infect additional devices. This formed a network of compromised connected objects under their control, effectively making them the botmasters. This army of infected machines could initiate various actions, including performing denial-of-service attacks on third-party servers.
After the gang was dismantled, it was discovered that one of their primary motivations for the attack was to carry out a saturation attack, specifically a denial of service against a competing group's Minecraft servers. These attackers operated multiple servers and sold subscriptions to players. By overpowering their competitors' servers, they aimed to eliminate any further connections and gameplay, driving players to abandon the rival servers and migrate to their own, where they would pay for subscriptions.
Fortunately, law enforcement apprehended and incarcerated these criminals, effectively ending their operations. Note they then worked with the FBI, according to Wired.
As we increasingly rely on various connected products, it is crucial to ensure their inherent security. Whether a solar panel or a smart thermostat, every device should be secured to prevent it from becoming a potential attack point.
Imagine a scenario where a group gains control over hundreds of solar panels delivered in an unsecured configuration and proceeds to attack these solar panels. This not only puts the owners of these panels in an embarrassing energy situation, but as our dependence on renewable energy grows, it becomes essential to maintain a continuous supply of energy. While it may be considered a nice-to-have today, with the ecological transition, it will become a must-have.
Introducing The EU Cyber Resilience Act
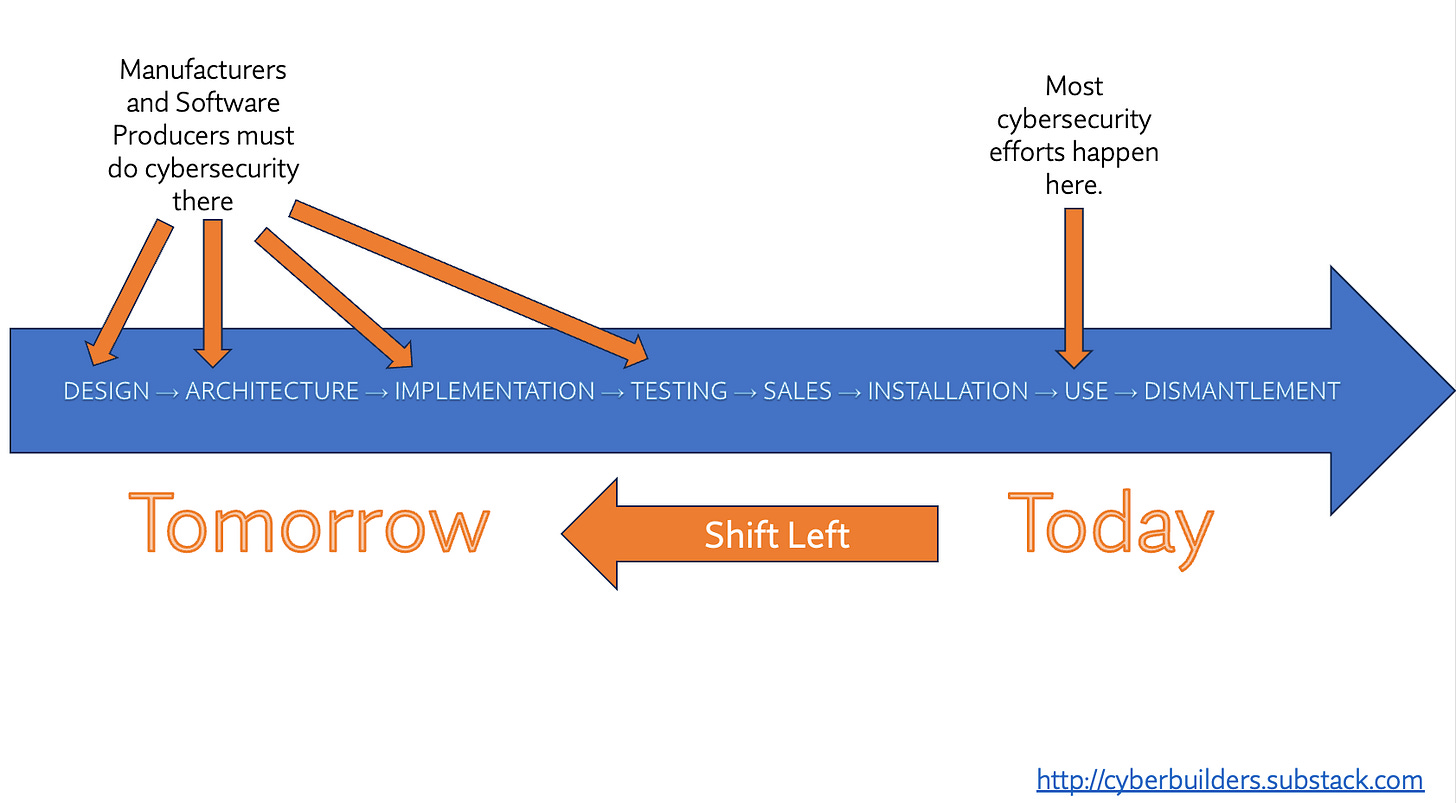
The EU Cyber Resilience Act, designed by the European Commission, aims to shift (”Shift Left”) the responsibility of product security from end-users to manufacturers. It insists that software designers and producers must implement security measures, freeing users from the burden of securing their devices.
In the EU Commission jargon, “products with digital elements” stands for IoT devices and all modern devices, as discussed in “Everyone is a Software Producer.”
The EU has identified two main objectives:
Promote developing secure products “with digital elements” by reducing vulnerabilities and ensuring manufacturers prioritize security throughout the product's life cycle.
Enable users to consider cybersecurity when choosing and using products with digital elements.
The EU Commission website lays down four objectives.
ensure that manufacturers improve the security of products with digital elements from the design and development phase and throughout the whole life cycle;
ensure a coherent cybersecurity framework, facilitating compliance for hardware and software producers;*
*enhance the transparency of security properties of products with digital elements, and
enable businesses and consumers to use products with digital elements securely.*
You can access the Cyber Resilience Act in all EU official languages

Show me the money - Who would they pay for these requirements?
Implementing cybersecurity to protect important properties is essential, although it significantly increases the engineering and operations costs. While consumer electronics, such as Bluetooth speakers, home network equipment, and home automation sensors, are now available at affordable prices, enhancing their security requires additional time, engineering, software, and hardware, increasing the overall cost. The impact would be even higher for industrial devices as the stakes are higher.
While necessary for user security, these measures will likely have a profound effect on the business models of software producers. They will need to factor these requirements into their design processes and throughout the lifecycle of their products. This will inevitably increase initial costs, monitoring costs, and infrastructure costs.
Software producers must change their attitudes towards users, recognizing that they cannot ignore their responsibilities. They must care for their entire software portfolio, including products manufactured several years ago.
The EU regulation lists engineering phase requirements and asks each manufacturer for an ambitious vulnerability program. Let's analyze the expectations of the Cyber Resilience Act one by one to understand better how it will shape future business models.
Security starts early in the engineering process.
The EU's first requirement aims for a significant shift in the responsibility of product security. Instead of expecting users to decipher potential risks and implement security protection to mitigate products not designed with any level of self-protection, the responsibility now lies with product vendors. They are expected to understand the environment where their products will operate, identify the associated risks, and design with an appropriate level of cybersecurity in mind.
The second requirement mandates the delivery of products without known vulnerabilities. Product designers must scrutinize their software, including code and third-party libraries, to identify and rectify potential weak spots. However, a crucial aspect often overlooked is monitoring vulnerabilities over time. This necessitates a dedicated team for software maintenance and security updates, a change that might be significant for manufacturers who only focus on software during the initial design phase.
📌 As the founder of Sentryo from 2014 to 2023, I worked on the cybersecurity of industrial systems in manufacturing, power grids, and transportation systems. I can assure you that most PLCs, programmable controllers, have no authentication system to modify their configurations, restart them, or stop them from functioning.
The plant must continue to operate, and these individualized password systems are often seen as essential for reliability and factory production. The tradeoff is not in favor of cybersecurity.
The third requirement aims to simplify product implementation and ensure security. It stipulates that products should be delivered with a secure configuration by default. This requirement acknowledges that end users may not have the expertise, time, or resources to configure the product securely. It also addresses the security risks posed by the quick installation of products that could be easy targets for cyber attacks or used as launchpads for more extensive breaches.
The fourth engineering requirement mandates that every product must have adequate access control mechanisms. These include user identification systems and authentication methods that establish a shared secret between the software user and the software itself, such as passwords or passphrases. Moreover, it emphasizes the need for traceability to track if someone has attempted to access a system, even if the access is legitimate.
Confidentiality, Integrity, Availability - The CIA Triad
When users entrust their data to a product, they expect that their information will remain confidential. Thanks to secure communication mechanisms like Transport Layer Security (TLS), confidentiality can be maintained even when data is transmitted over networks. But remember, no security mechanism is invincible. Cryptography best practices may recommend specific algorithms or key sizes at one point, but the landscape can change radically in a few years. Therefore, manufacturers should continuously update their encryption methods to keep up with changing technologies and emerging vulnerabilities.
Data integrity, often mistaken for confidentiality, is a distinct requirement. It's not about keeping data secret; it's about ensuring that no one tampers with the data. Whether it's a configuration parameter, a database entry, or a file on a hard drive, data integrity checks ensure that changes are only made by authorized personnel. An excellent example of this is ensuring that any update is signed by the publisher, thus authenticating the source and ensuring the update file's integrity.
The availability of a product or service might seem like a given, but it's more complicated than it appears. Manufacturers often try to reduce costs and increase margins by opting for limited hardware, which could lead to significant availability issues if the product is used beyond its intended capabilities.
For instance, IoT devices with simple, low-cost processors can easily be overwhelmed by commercial PC doing some network saturation - a simple ping flood using ping -f a.b.c.d might work - manufacturers need to limit the impact of a product's failure on other systems, ensuring that it doesn't emit harmful signals or consume excessive resources.
Lastly, the European Commission stipulates that a product should only collect and process personal data when necessary. This requirement, aligned with the General Data Protection Regulation (GDPR), ensures that no personal data is collected without the user's knowledge or consent.
Logging activities of devices is needed for security but it is hard to implement
Furthermore, one requirement states that manufacturers must ensure the cyber robustness of the software and the availability of logs and traces.
Tracing all security-related events within the system is a recommended practice for cybersecurity. Still, the purpose of this trace should be clarified. Is it intended for end users or experts? Implementing a cybersecurity solution that traces access attempts, detects errors, and securely sends data to a central collection center requires significant effort. Experts can utilize this data to detect vulnerabilities, understand criminal techniques, identify malicious activities, and enhance protection.
But what would be the usage of the data? Many of these logs are useless for an end-user as they don’t have a deep view of the device and software architecture. They might be alarmed by a benign log or miss a real anomaly.
That’s why manufacturers should implement flight recorders that provide the needed information for experts to do forensics. It will drive implementation to focus on information needed by experts to understand what happened and issue recommendations.
Vulnerability management is a central practices for software producers.
The EU Cyber Resilience Act stipulates that all entities producing software-infused products must establish a vulnerability management protocol. They are required to identify and document any vulnerabilities present in their software. This documentation must include a software 'Bill of Material'— a comprehensive inventory of the contents of their software.
Entities must promptly address identified vulnerabilities by providing security patches. Regular security reviews and tests must be conducted to ensure the ongoing robustness of their software. Once vulnerabilities have been addressed and updates made available, entities must disclose the existence of past vulnerabilities and their impacts publicly. This openness allows users to understand the nature of the flaw and its potential impacts, informing their decision on whether or not to update the software.
This vulnerability management process is not an optional extra but a company-wide policy. Entities must also liaise with relevant authorities in their country, sharing their vulnerability knowledge and expertise.
The EU Act also mandates a simplified and secure mechanism for distributing updates. The era of complicated update processes on inaccessible company servers is over. Instead, updates should be easily accessible, as easy as pressing 'yes' when your phone suggests an update. Importantly, these updates must be provided free of charge to all users.
Conclusion
In conclusion, the Cyber Resilience Act is a crucial step toward ensuring the security of all software-infused products. It mandates producers to adopt a proactive approach towards vulnerability management, providing regular updates and maintaining transparency with users and authorities. As we move towards an increasingly digitized world, such measures are essential to safeguard our digital infrastructure and protect users from potential security threats.
Can I ask you a favor? Share this article with your Cyber Builders peers. Give me some “Like” on social media; it will help promote my work.
Laurent 💚