Cyber Builders: A Collaborative Approach to Cybersecurity
Listening to Our Community: The Vision Behind Cyber Builders and Our Quarterly Survey Results
Welcome back to the Cyber Builder substack, where we delve into topics about how you can navigate and shape your pathway into the fascinating world of cybersecurity.
You and I know that cyber isn’t a one-and-done deal; it’s a journey. That's why I am honored to walk this path with you as we build, learn, and shape the future of Cyber Builders.
I'll share the stats of my quarterly survey. Thanks for participating! I will start this newsletter with a brief overview of the Cyber Builders project, reflecting on my vision and sharing how I see your roles.
Cyber Builders Overview
The cybersecurity landscape today is a vast arena. It has become an increasingly complex ecosystem where myriad vendors, clubs, professional associations, and individual players operate. Each has a unique role, and though they all cohabit in the vast digital realm, they often function more like isolated islands rather than a unified landmass.
This fragmentation often leads to a need for more communication and collaboration, which is critical to developing comprehensive cybersecurity measures. There is diverse expertise from vendors, users, resellers, consultants, and entrepreneurs, presenting a wealth of knowledge that can be extremely valuable when shared and utilized collaboratively. Unfortunately, such cross-pollination of ideas and strategies is few and far between.
Enter Cyber Builders. Rather than being another player in the crowded field, Cyber Builders is a beacon calling for cohesion and collaboration. It's a collaborative space that connects the dots and bridges the gaps in the vast cybersecurity landscape.
At its core, Cyber Builders is a newsletter that facilitates knowledge transfer across all groups. It provides a unique platform where entrepreneurs, vendors, users, resellers, consulting entities, and more can share insights, debate strategies, and work together on practical daily operations issues.
Cyber Builders is more than just a platform - it is a catalyst for change, advocating for a collaborative approach to addressing cybersecurity challenges in our increasingly digital world. Through this synergy, Cyber Builders is willing to redefine best practice norms and push the boundaries of what's possible in cybersecurity.

The Value of Collaboration in Cybersecurity
Exploring Roles and Their Values
In the cybersecurity landscape, each player has a unique and invaluable role. Entrepreneurs are the ultimate innovators, turning bold ideas into groundbreaking solutions. Service providers, on the other hand, ensure the practical application of these solutions, tailoring them to the unique needs of their clients. Security practitioners, whether in a small or large business, then serve as the immediate line of defense, leveraging these services and solutions to safeguard their respective organizations.
Understanding these roles and how they interact and complement each other is crucial in driving effective cybersecurity measures. Collaborative efforts among these players allow for a more comprehensive approach to security, turning isolated efforts into a cohesive and securely knit cyber defense.
It’s all about empathy. Empathy for security practitioners from vendors prevents them from pushing their marketing messages without listening and solving practical issues. Empathy for the vendor by security practitioners and resellers understand the challenge of being an entrepreneur, raising money to fuel its engineering and product-building activities.
It also understands that technology is neither good nor bad. It’s a technology, and security needs to be applied. As an example, Generative AI falls in that bucket today.
Case Studies
Take a look at these resources, each article showcasing a practical application of such collaborations:
AI and Security: The worlds of AI and cybersecurity have started to intertwine, creating a progressive yet potentially perilous frontier. In "AI Pass Hacker Test - GPT-4's Remarkable Performance in CEH Exam", we see the implications of AI in terms of penetration testing. Meanwhile, "AI Security Engineering is Needed, Not Emotions" emphasizes the critical role of security engineering in shaping AI's future.
Product Building and Entrepreneurship: The process of creating cybersecurity solutions is intricate. It requires knowledge, skill, and a clear understanding of the market's landscape. The articles "2023 Q1 - State of the VC Market for Cybersecurity", "The Six Pillars of Cybersecurity Platforms, "Unlocking the Secrets of Cybersecurity Product Teams" provide insight into this venture, explaining how cybersecurity platforms can create value and discuss entrepreneurship's crucial role.
General trends: Recognizing trends in cybersecurity is essential to navigate this rapidly evolving field. "Resilience is the New Black" shows how resilience transforms cybersecurity, while "Why Building Cybersecurity Solutions Remains Critical" highlights the continued need for innovative cybersecurity platforms. Reflecting on events like "RSA 2023 - Platforms, AI, and 400 vendors" offer additional perspectives from the cybersecurity community.
SMB and CyberSecurity: Small and Medium Businesses (SMBs) are pivotal players in the cybersecurity landscape, needing to stay persistently informed despite any in-house expertise. They form a set of markets or niches, not a 'one size fits all' approach, necessitating market segmentation that factors in industry specifics and unique skill sets. Managed services are still missing to offer potent solutions to SMBs' unique challenges and remain misunderstood or under-utilized. Unraveling this complexity exposes SMBs to many cybersecurity solutions well suited to their peculiar risks and business goals. Finally, the key to SMB cybersecurity success is understanding and integrating certain critical elements, not just a good product.
Survey Results
A good NPS
NPS, or Net Promoter Score, is a customer loyalty metric that measures how likely customers are to recommend a company or product to others. In the context of Cyber Builders, I asked, “How likely would you recommend Cyber Builders to your peers in cybersecurity, friends, or colleagues?" to gauge how satisfied subscribers are with the content and whether they would recommend it to others in their network. The NPS score is calculated by subtracting the percentage of detractors (those who respond with a score of 0-6) from the percentage of promoters (those who respond with a score of 9-10). The result ranges from -100 to 100, with a higher score indicating higher customer loyalty and satisfaction. Industry benchmarks vary by sector, but a score above 50 is considered excellent.
In the survey 2023 Q2, I got these results.
Which leads to an NPS of 45, which is good. I guess that I have 55% of “passives” subscribers indicates that I need to double down on making them happier in Q3 onwards. It’s great also that after a quarter, no one is a “detractor”! 😅
A diverse audience
The audience is very diverse. A large pool (40%) comes from the cybersecurity vendor industry, but most are service providers or cybersecurity practitioners.
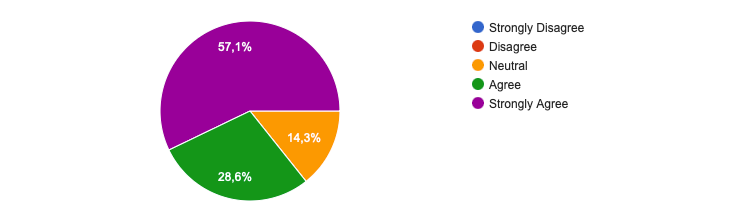
Topics for the future
AI is the 2023 major topic, so it is no surprise that it gets the most “Strongly Agree” votes.

I described previously what I have in mind for the various topics in the post “Cyber Builders Checkpoint: Reflect, Review, and Revamp.”
I see that the top winner (85% of Agree/Strongly Agree) is a deep dive into the different trends, be assured that I’ll keep covering it. I have that list of trends as a backlog:
Resilience: Ensuring systems keep functioning even under attack through risk management, threat intelligence, and incident response.
Open-Source Intelligence (OSINT): Gathering intelligence on potential security threats using publicly available information.
Internet of Things (IoT) Security: Addressing the increased threat surface that comes with the increased connectivity of IoT.
AI and CyberSecurity: How to use Generative AI in Cyber Security products. What do you think about it?
Shift Left and Developer Tools: Integrating security into the software development life cycle (SDLC) from the beginning to reduce vulnerabilities in the final product.
Zero Trust: A security model that assumes all users, devices, and applications are untrusted until proven otherwise, requiring strict access controls and continuous monitoring.
Cloud Security: A comprehensive security strategy that includes access controls, data encryption, and threat detection for data and applications in the cloud.
Data Security: A multi-layered approach including encryption, access controls, and continuous monitoring to protect sensitive data stored or transmitted across devices and networks.
Human in the Loop: Ensuring system and data security through security policies, education, and monitoring.
Conclusion
Cyber Builders continues to be a beacon of collaboration in the dynamic world of cybersecurity. Your ongoing participation is invaluable, enriching our platform with diverse perspectives and leading-edge insights.
I'm excited to explore your preferred topics. ALL WILL BE ADDRESSED, from AI and cybersecurity to managing security teams to decoding general trends. After all, this is your platform, driven by your input and interests. Here's to a future built on collaboration, understanding, and shared knowledge!
Stay tuned for more insights and discussions as we continue our endeavor to build a safer digital world together.
Best
Laurent 💚